What are ASR rules?

Attack Surface Reduction (ASR) rules are a set of security controls implemented in modern operating systems, such as Windows 10 and Windows Server 2016 and above, to mitigate the risk of cyberattacks. The ASR rules aim to reduce the "attack surface" of the operating system, meaning the areas where an attacker can potentially exploit vulnerabilities to gain unauthorized access or cause harm to the system.
ASR rules typically involve configuring security settings and restrictions on specific system functions and features to prevent malicious actors from exploiting them. For example, ASR rules may disable scripting engines or block access to specific types of executable files, such as macros or PowerShell scripts. ASR rules can also limit the use of web browsers or prevent the execution of unsigned code.
You can think of ASR rules as secondary to the firewall and malware filters. Let's take an example, Joe Gruber is an accountant working at Gitbit. He receives an email that says it's from the bank and he's late on a payment. Attached to the email is a PDF. Some malicious code inside the PDF will first create a child process. Then from that child process, it will infect Joe's computer with ransomware. Somehow that email has gone passed your anti-spam and anti-malware email filters and the anti-virus on Joe's computer isn't picking up the malicious PDF either. Fortunately, you've put the ASR rule in place that blocks Adobe from creating child processes in place. Yay! No infection.
The ASR rules can be deployed using group policies, configuration managers, or other security management tools. ASR rules are an important part of the defense-in-depth security strategy, which involves implementing multiple layers of security controls to protect the system from cyber threats. By reducing the attack surface, ASR rules help to prevent the exploitation of vulnerabilities and reduce the impact of successful attacks on the system.
What are the different types of attack surface reduction rules that can be put in place?
Attack surface reduction (ASR) rules are security measures that aim to reduce the opportunities for attackers to exploit vulnerabilities in a system. The specific types of ASR rules that can be put in place depend on the system and the security requirements. Here are some examples:
- Network-based rules: These rules restrict network traffic to and from the system. Examples include firewall rules, network segmentation, and traffic filtering.
- Application-based rules: These rules restrict access to applications and their features. Examples include disabling unused services, disabling macros, and blocking file extensions.
- Identity and access management (IAM) rules: These rules restrict access to the system based on user identity and privileges. Examples include multi-factor authentication, least privilege access, and role-based access control.
- Device-based rules: These rules restrict access to the system from specific devices. Examples include device identification and authentication, and device trust.
- Configuration-based rules: These rules restrict access to system configurations that could be exploited by attackers. Examples include disabling unnecessary ports, services, and protocols, as well as disabling default accounts and passwords.
- Patching and updates: Regular patching and updates are crucial for reducing the attack surface. Updates should be applied to all components of the system, including operating systems, applications, and firmware.
These are just a few examples of the types of ASR rules that can be put in place. Effective ASR requires a multi-layered approach that incorporates several of these types of rules, tailored to the specific system and its security requirements.
How do you put ASR rules in place?
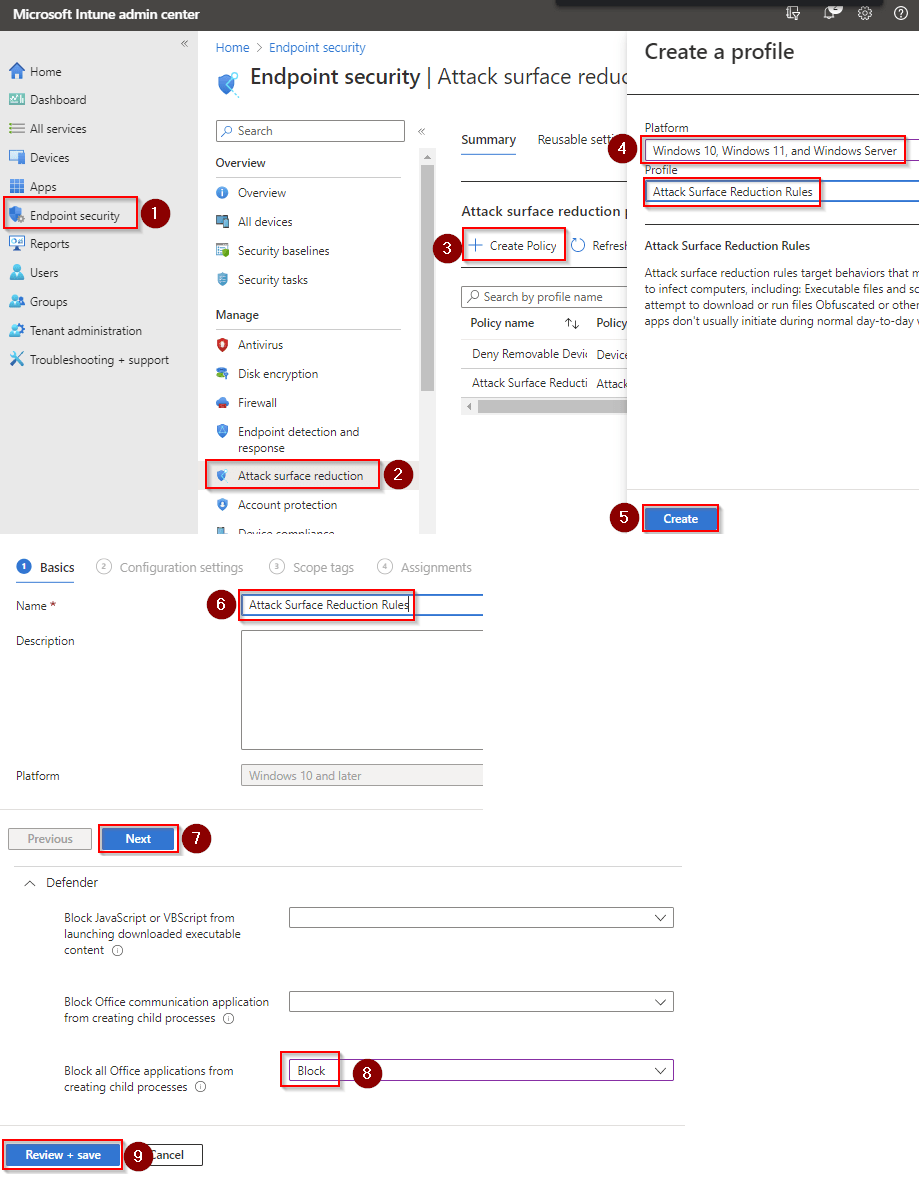
The short, answer is you use Microsoft Defender antivirus with Real-Time Protection and Intune. Here's a quick rundown of all the attack surface reduction rules I recommend putting in place:
- Use advanced protection against ransomware
- Block executable files from running unless they meet a prevalence, age, or trusted list criterion
- Block Win32 API calls from Office macros
- Block Office applications from creating executable content
- Block all Office applications from creating child processes
- Block persistence through WMI event subscription
- Block abuse of exploited vulnerable signed drivers
- Block Office applications from injecting code into other processes
- Block process creations originating from PSExec and WMI commands
- Block Office communication application from creating child processes
- Block Adobe Reader from creating child processes
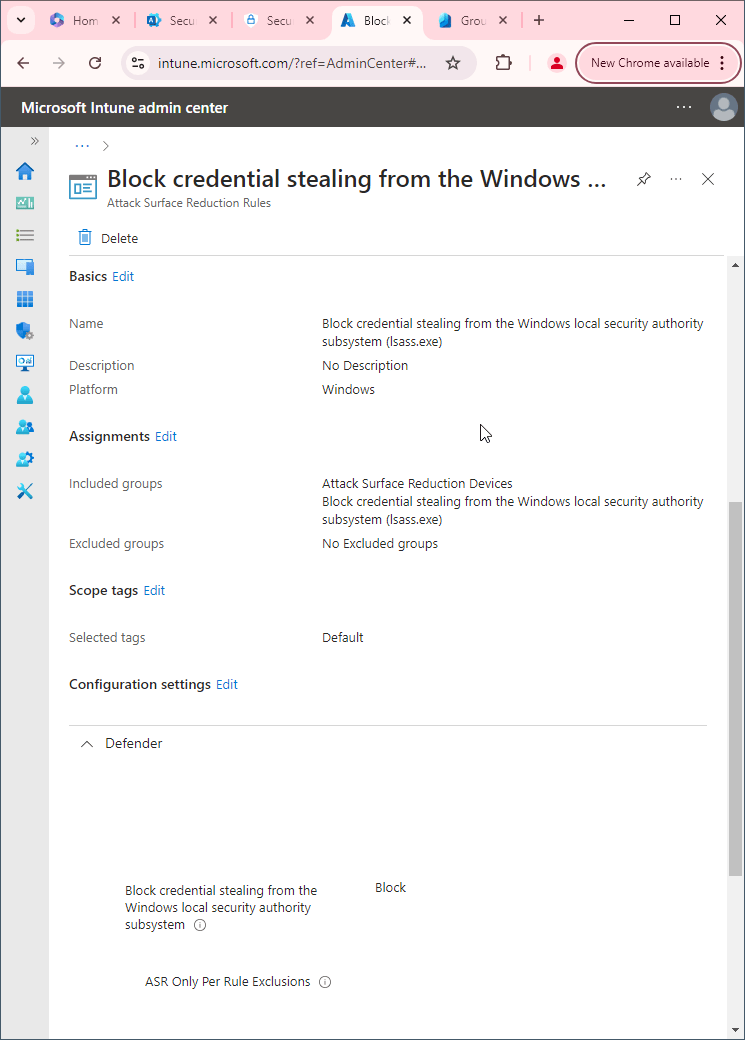
- Block credential stealing from the Windows local security authority subsystem (lsass.exe)
- Block executable content from email client and webmail
- Block execution of potentially obfuscated scripts
- Block untrusted and unsigned processes that run from USB
- Block JavaScript or VBScript from launching downloaded executable content
Troubleshoot attack surface reduction rules
There are a number of issues that can cause the ASR rules to not work as expected. Typically, it falls into 3 categories:
- false positive: Something is blocked that shouldn't be blocked.
- false negative: Something isn't blocked that should be blocked.
- Error / Noncompliant: Something is preventing the rule from applying to the device.
How to monitor ASR rules
Monitoring ASR rules to see what's being blocked is pretty simple if you know where to go.

- Go to Microsoft 365 Defender admin center > Hunting > Advanced Hunting.
- Type the following text in the Query: DeviceEvents | where ActionType startswith "Asr"
- Click Run query.
There you'll see all the ASR rules that have blocked content and on what device. By clicking on one of the results you'll receive more information about the alert. To filter the results on the computer you can run the following: DeviceEvents | where ActionType startswith "Asr" and DeviceName contains "Device01" (replace Device01 with your computer name).