Block credential stealing from the Windows local security authority subsystem (lsass.exe)
Attack Surface Reduction (ASR) rules are the most effective method for blocking the most common attack techniques being used in cyber attacks and malicious software.
This ASR rule locks down LSASS.
This security control is only applicable for machines with Windows 10, version 1803 or later.
Attackers can use tools like Mimikatz to scrape cleartext passwords and NTLM hashes from LSASS.
Why would you want to Block credential stealing from the Windows local security authority subsystem (lsass.exe)?
Prevention of credential theft from the Windows Local Security Authority Subsystem Service (LSASS) is Important to block many attacks that rely on stealing these credentials:
Credential theft prevention:
Usernames and passwords of users and passwords of domain administrators are very vital things, which are stored in the LSASS process because once this information is seen by attackers, they can pivot into the network, escalate privileges, and compromise other systems.
Ransomware attack mitigation:
One other common area to block in ransomware attacks is the credential theft from LSASS. If you block this, you reduce one avenue the attacker would normally use to gain the access they need to deploy ransomware across your network.
Blocking Improves Security Posture On the Whole:
Applying this rule is just a part of many other Attack Surface Reduction (ASR) rules in Microsoft Defender for Endpoint, which, in concert, serve to harden your systems against different categories of attacks, thereby making it more difficult for attackers to exploit vulnerabilities in the first place.
How to block credential stealing from the Windows local security authority subsystem (lsass.exe)
First, you'll need to make sure Microsoft Defender Antivirus is turned on as the primary antivirus solution, with Real-Time Protection enabled. To verify Defender Antivirus is turned on with real-time protection enabled go to Security recommendations and search for "Turn on real-time protection". From there click "Turn on real-time protection". Finally, click Exposed devices
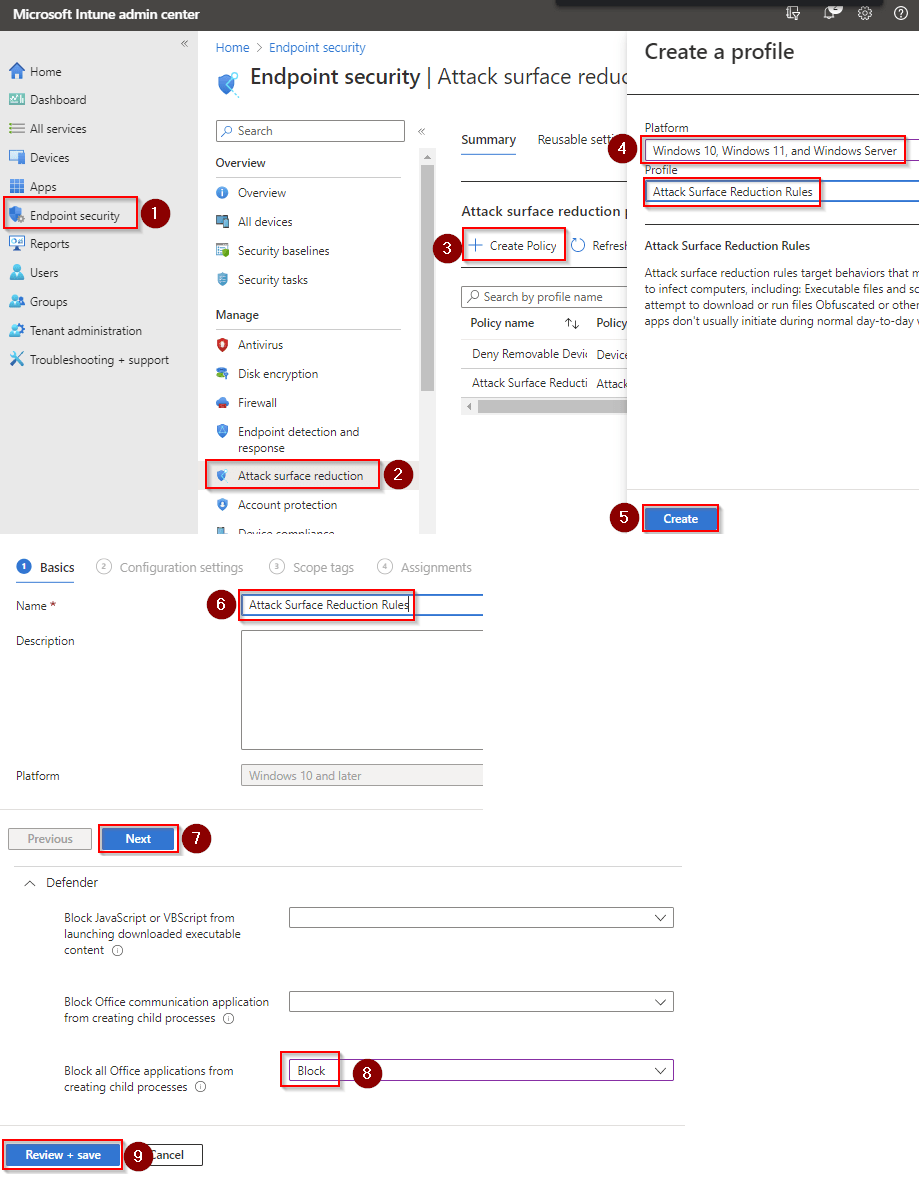
- Go to Microsoft Intune admin center (Microsoft Endpoint Manager) > Endpoint security > Attack surface reduction.
- Click Create Policy.
- Set Platform to Windows 10 Windows 11, and Windows Server.
- Set Profile to Attack Surface Reduction Rules.
- Click Create.
- Name your policy and click Next.
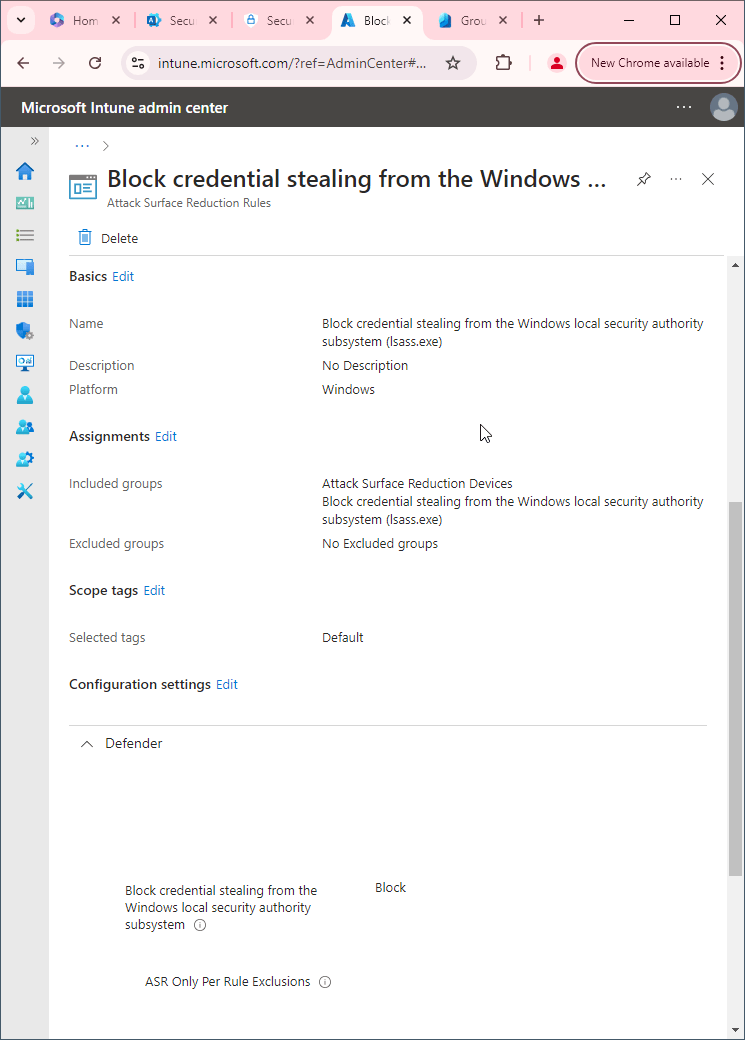
- Set Block credential stealing from the Windows local security authority subsystem to Block. Click Next.
- Add your inclusions and exclusions. Click Next > Next > Create.