Block process creations originating from PSExec and WMI commands
"Block process creations originating from PSExec and WMI commands" is a security feature in Microsoft 365 that helps prevent unauthorized access and malicious activity on your systems. PSExec and WMI are commonly used tools that allow remote access to other systems, which makes them attractive targets for attackers seeking to gain access to your network.
The "Block process creations originating from PSExec and WMI commands" feature works by monitoring system events and blocking any attempts to create processes from PSExec and WMI commands. This means that any attempts to remotely execute commands using PSExec or WMI will be prevented, even if the attacker gains access to your network.
By blocking these types of commands, the feature helps to prevent attackers from moving laterally across your network, escalating privileges, and accessing sensitive data or resources. It can also help to detect and prevent the spread of malware, ransomware, and other types of malicious software that may be executed through these commands.
Overall, this feature provides an added layer of security to your Microsoft 365 environment, helping to protect your systems and data from unauthorized access and malicious activity. It is recommended to enable this feature as part of your overall security strategy.
Why would you not want to block process creations originating from PSExec and WMI commands?
Some legitimate IT tools and applications may use PSExec and WMI commands to perform system management tasks, and blocking these commands could cause conflicts or interruptions in workflow. For example, SCCM uses WMI to install software on devices. If you're still using SCCM to deploy any software you won't want this rule enabled.
How to block process creations originating from PSExec and WMI commands
First, you'll need to make sure Microsoft Defender Antivirus is turned on as the primary antivirus solution, with Real-Time Protection enabled. To verify Defender Antivirus is turned on with real-time protection enabled go to Security recommendations and search for "Turn on real-time protection". From there click "Turn on real-time protection". Finally, click Exposed devices.

Now that our devices are ready, let's go ahead and block process creations originating from PSExec and WMI commands using Intune.

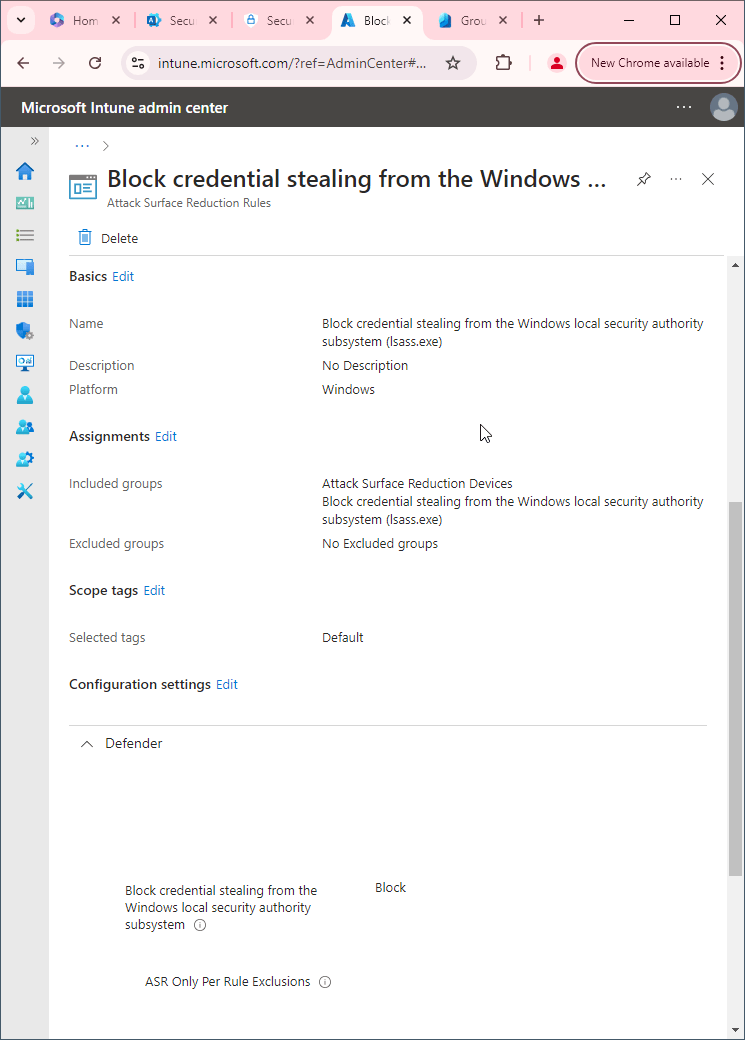
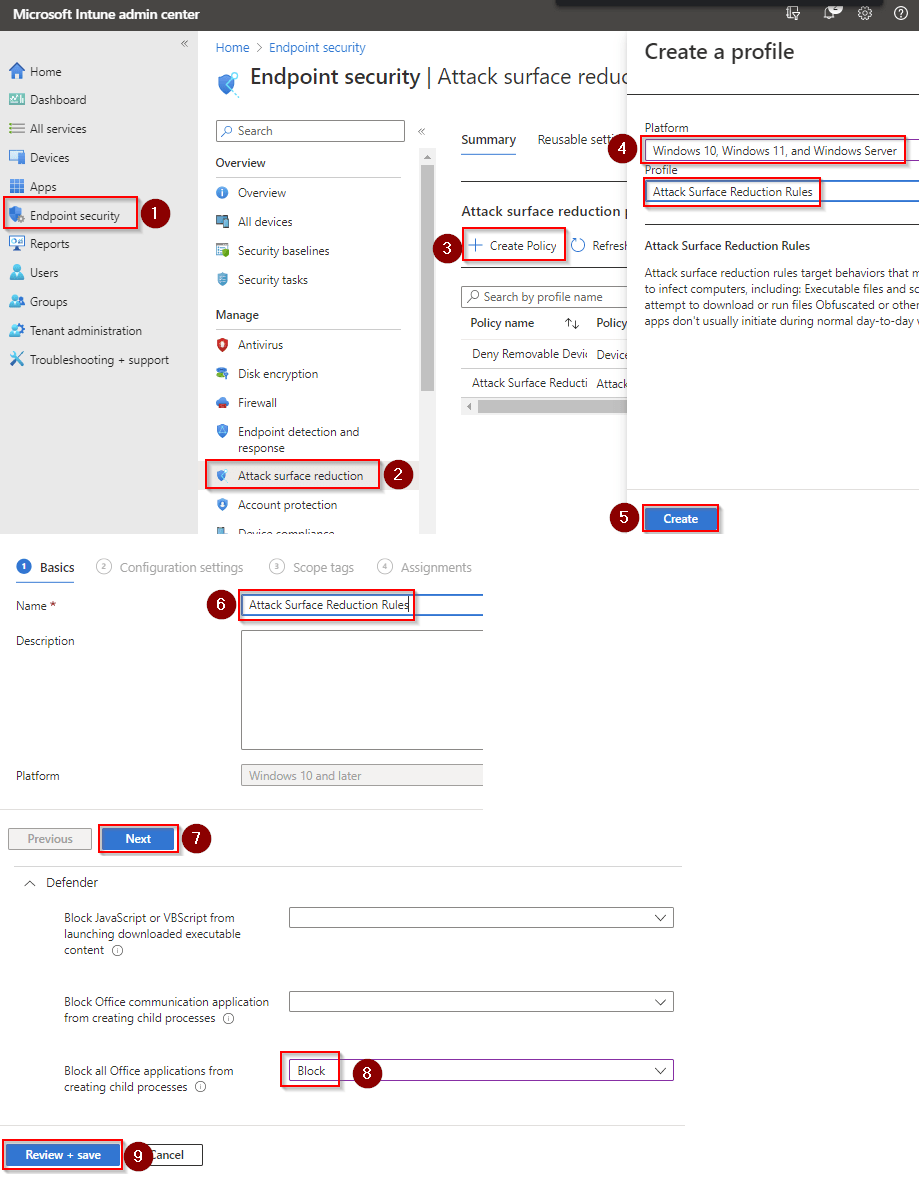
- Go to Microsoft Intune admin center (Microsoft Endpoint Manager) > Endpoint security > Attack surface reduction.
- Click Create Policy.
- Set Platform to Windows 10 Windows 11, and Windows Server.
- Set Profile to Attack Surface Reduction Rules.
- Click Create.
- Name your policy and click Next.
- Set Block process creations originating from PSExec and WMI commands to Block. Click Next.
- Add your inclusions and exclusions. Click Next > Next > Create.