Block persistence through WMI event subscription
Before we can jump into this one, let's break it down into different parts.
What's WMI?
WMI stands for Windows Management Instrumentation, which is a powerful technology built into the Windows operating system that allows for the management and monitoring of system resources. It provides a standard way for applications and system administrators to access and manage Windows system information, settings, and performance data.
WMI is a comprehensive infrastructure for managing and accessing data and resources in Windows operating systems. It exposes a wide range of information about the operating system, hardware, software, and applications running on a Windows machine. This information can be accessed through a variety of interfaces, including scripting languages such as PowerShell and VBScript, as well as through programming languages like C++ and .NET.
WMI enables system administrators to automate system management tasks, monitor system performance, and respond to system events in real-time. It provides a powerful and flexible way to manage Windows systems, and is widely used in enterprise environments for tasks such as software deployment, system inventory, and security management.
In summary, WMI is a powerful technology built into Windows that provides a standardized way to manage and access information about Windows systems and resources.
Why would you not want to block persistence through WMI event subscription?
Blocking persistence through WMI event subscription can be useful for security purposes, as it can prevent attackers from establishing persistent access to a compromised system. However, there may be some situations where you would not want to block persistence through WMI event subscription.
For example, some legitimate applications or tools may use WMI event subscriptions to monitor system events or automate certain tasks. Blocking all WMI event subscriptions could potentially interfere with the functionality of these applications.
Additionally, if you are using WMI event subscriptions as part of your own security monitoring or management system, blocking all subscriptions could prevent you from receiving important alerts or updates about the system.
Ultimately, the decision to block persistence through WMI event subscription should be based on a careful assessment of the risks and benefits in your specific situation.
How to block persistence through WMI event subscription
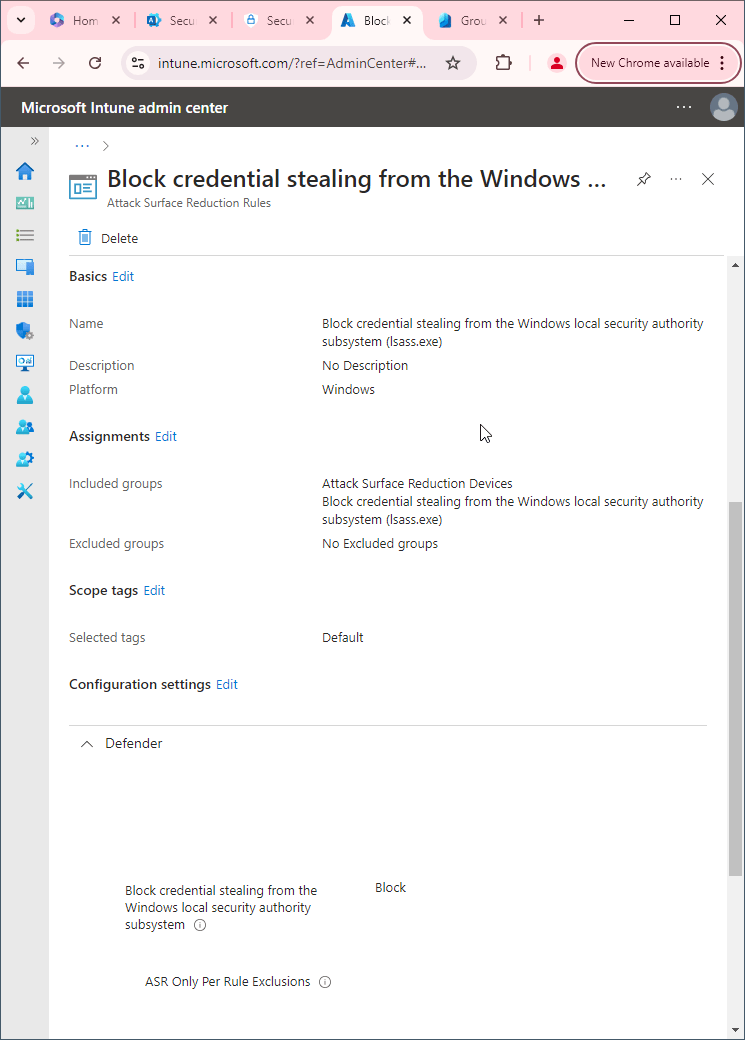
First, you'll need to make sure Microsoft Defender Antivirus is turned on as the primary antivirus solution, with Real-Time Protection enabled. To verify Defender Antivirus is turned on with real-time protection enabled go to Security recommendations and search for "Turn on real-time protection". From there click "Turn on real-time protection". Finally, click Exposed devices.

Now that our devices are ready, let's go ahead and block persistence through WMI event subscription using Intune.

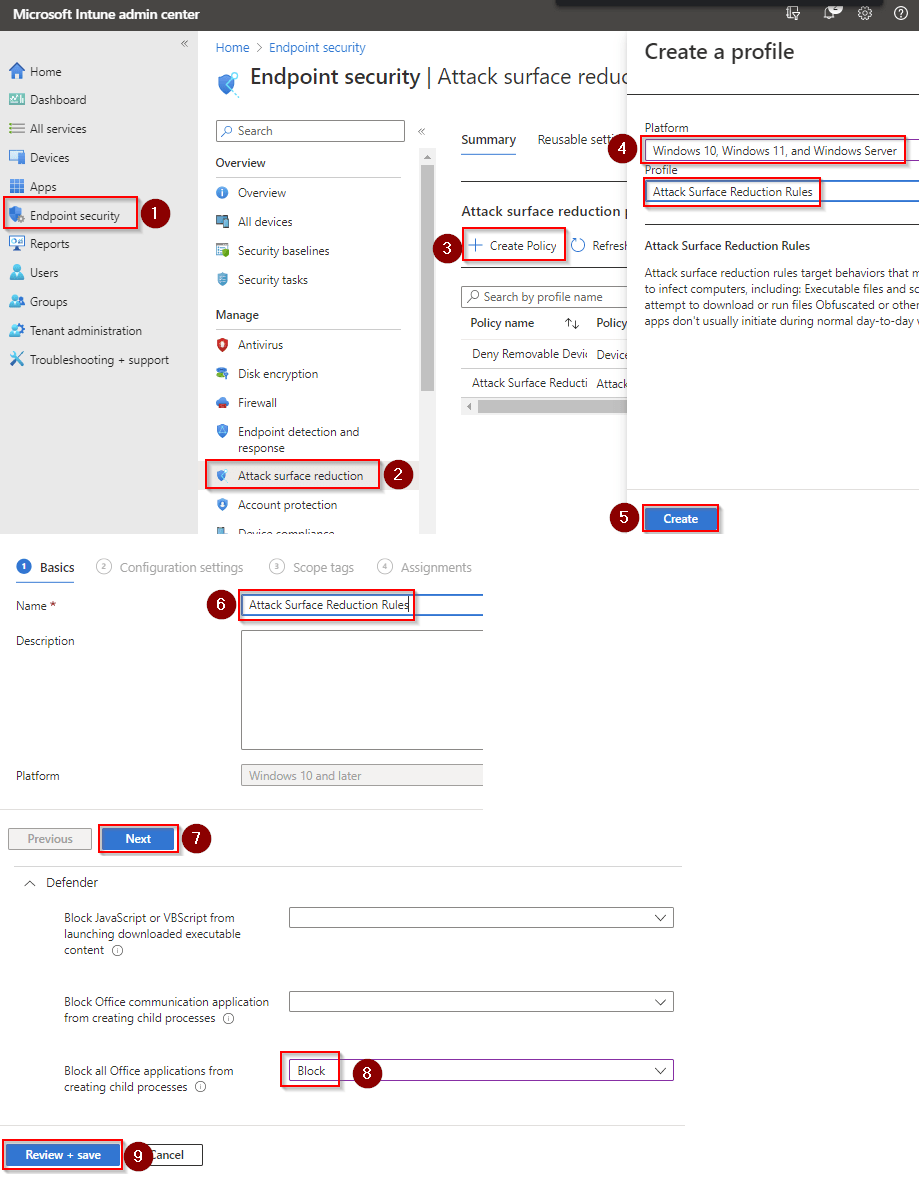
- Go to Microsoft Intune admin center (Microsoft Endpoint Manager) > Endpoint security > Attack surface reduction.
- Click Create Policy.
- Set Platform to Windows 10 Windows 11, and Windows Server.
- Set Profile to Attack Surface Reduction Rules.
- Click Create.
- Name your policy and click Next.
- Set Use advanced protection against ransomware to Block. Click Next.
- Add your inclusions and exclusions. Click Next > Next > Create.