Block Office applications from injecting code into other processes
Blocking Office applications from injecting code into other processes can help protect your computer from malicious code that could potentially compromise your system or steal your personal information.
Code injection is a technique where malicious code is injected into a running process, such as a web browser or another application, in order to take control of the process and execute commands. Code injection can be used to perform a variety of malicious actions, such as stealing passwords, hijacking sessions, or downloading additional malware onto the victim's computer.
Office applications can potentially inject code into other processes, such as web browsers, through the use of browser extensions or ActiveX controls. While these features can be useful for certain tasks, they can also be used to inject malicious code into web pages or other applications.
By blocking Office applications from injecting code into other processes, you can help reduce the risk of malicious code executing on your computer. This can be done by configuring security settings in the Office applications or by using third-party tools to monitor and block code injection attempts.
Why would you want to allow Office applications to inject code into other processes?
There are some legitimate reasons why you may want to allow Office applications to inject code into other processes. Here are a few examples:
- Browser extensions: Some Office applications, such as Microsoft Excel, have browser extensions that allow them to interact with web pages and other online content. These extensions can be useful for tasks such as importing data from a web page into a spreadsheet or exporting data from a spreadsheet to a web form.
- Integrations with other applications: Office applications can be integrated with other applications, such as CRM software or project management tools, to streamline workflows and improve productivity. These integrations may require Office applications to inject code into other processes in order to share data or interact with the other application.
- Customizations and add-ins: Office applications can be customized with add-ins and other tools that extend their functionality. These customizations may require Office applications to inject code into other processes in order to interact with the operating system or other applications on the user's computer.
While allowing Office applications to inject code into other processes can provide some benefits, it's important to weigh these benefits against the potential security risks. Malicious code injection attacks are a common tactic used by cybercriminals to compromise computers and steal sensitive information, so it's important to carefully evaluate the risks and benefits of allowing code injection on your computer. If you do decide to allow code injection, be sure to implement appropriate security measures, such as using antivirus software and keeping your software up to date with the latest security patches.
How to block Office applications from injecting code into other processes
Blocking Office applications from injecting code into other processes can help reduce the risk of malicious code executing on your computer. Here are some ways you can block code injection:
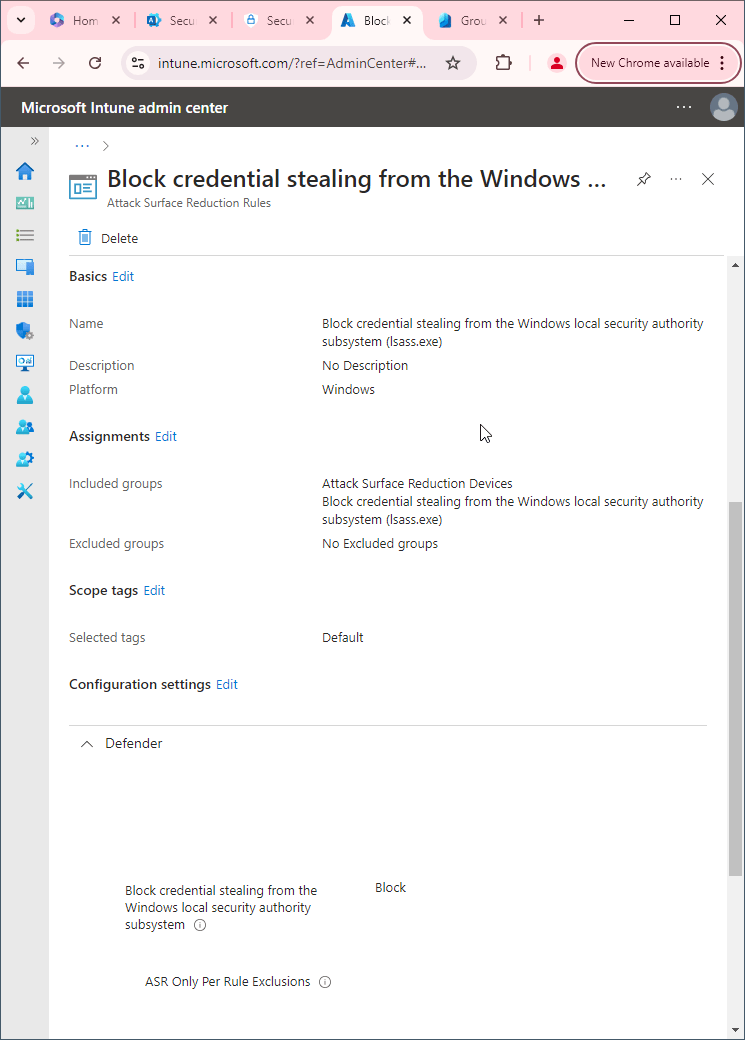
- Intune: You can create an attack surface reduction rule in Intune and apply it to your computers. You'll need Defender antivirus running with real-time protection enabled for it to apply though.
- Configure Group Policy settings: If you're using a Windows-based network, you can use Group Policy settings to disable code injection for all users on your network. This can be done by configuring settings in the Group Policy Editor, such as disabling browser extensions or restricting access to certain features.
How to block Office applications from injecting code into other processes using Intune
First, you'll need to make sure Microsoft Defender Antivirus is turned on as the primary antivirus solution, with Real-Time Protection enabled. To verify Defender Antivirus is turned on with real-time protection enabled go to Security recommendations and search for "Turn on real-time protection". From there click "Turn on real-time protection". Finally, click Exposed devices.

Now that we know our devices are ready, let's go ahead and block Office applications from injecting code into other processes.

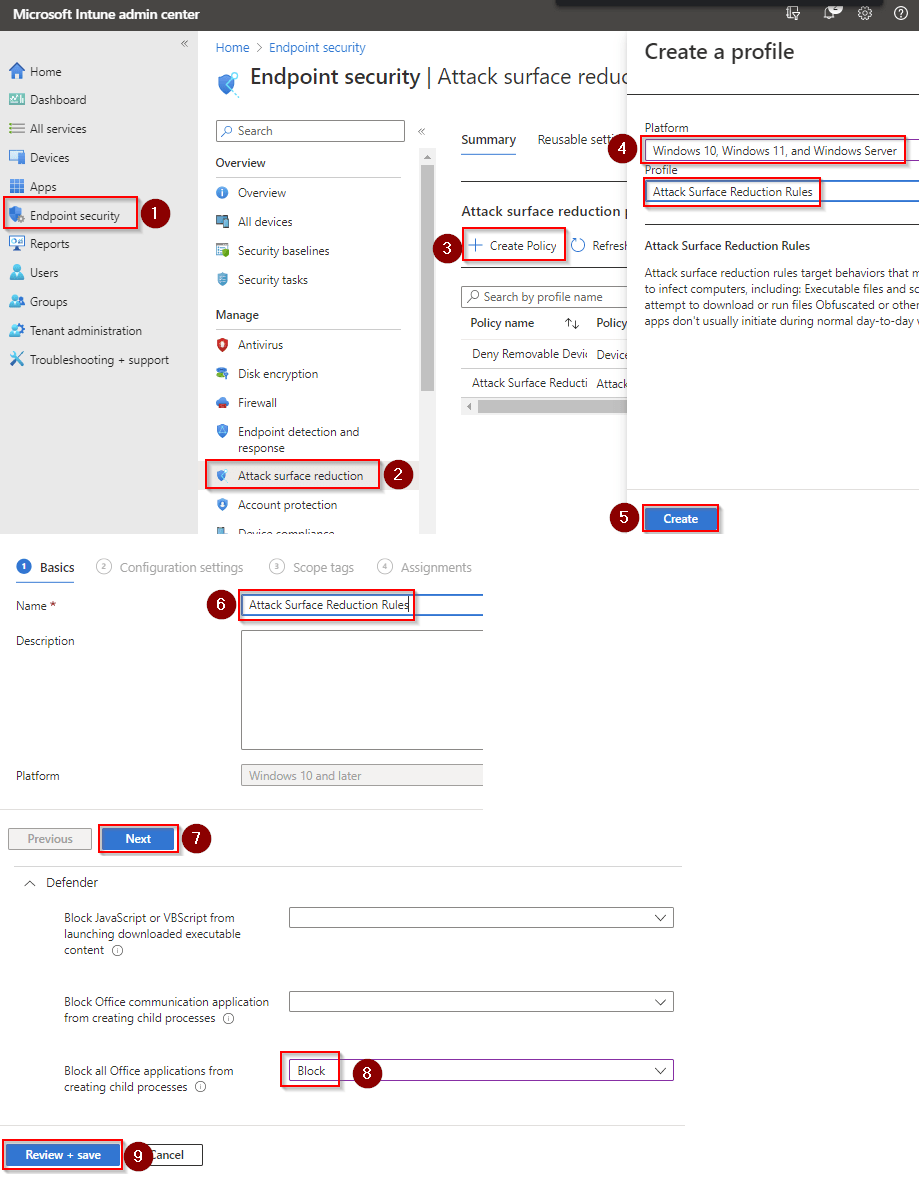
- Go to Microsoft Intune admin center (Microsoft Endpoint Manager) > Endpoint security > Attack surface reduction.
- Click Create Policy.
- Set Platform to Windows 10 Windows 11, and Windows Server.
- Set Profile to Attack Surface Reduction Rules.
- Click Create.
- Name your policy and click Next.
- Set Block Office applications from injecting code into other processes to Block. Click Next.
- Add your inclusions and exclusions. Click Next > Next > Create.