Block Office applications from creating executable content
Allowing executable content to be created from the Office app can be risky because it can potentially allow malicious actors to execute code on your computer without your knowledge or consent. Malicious executable content can include viruses, malware, or other types of malicious software that can harm your computer or steal your personal information.
Creating executable content from the Office app typically involves using a scripting language, such as Visual Basic for Applications (VBA), to create macros that automate certain tasks. While macros can be useful for automating routine tasks, they can also be used to execute malicious code.
Hackers can use a variety of techniques to trick users into running malicious macros, such as disguising them as legitimate documents or emails. Once a user runs the macro, the malicious code can execute on their computer, giving the attacker access to sensitive information, such as login credentials, financial data, or personal files.
To protect against this type of attack, it's important to block the Office suite's ability to create executable content.
Why would you want to allow Office to create executable content?
If you have an add-on or process where creating executable content from the Office suite you may not want to put this policy in place.
How to block Office applications from creating executable content
Here are some ways to block executable content creation:
- Intune: If you are using Microsoft 365's Intune then you can easily block Office applications from creating child processes. It's as simple as creating an attack surface reduction rule.
- Disable macro settings: The easiest way to block executable content creation is to disable macro settings in Office applications. This can be done by going to the "File" menu, selecting "Options," and then selecting "Trust Center." From there, you can disable macros or configure the settings to prompt you before enabling macros.
- Configure Group Policy settings: If you're using a Windows-based network, you can use Group Policy settings to disable macro settings for all users on your network. This can be done by configuring settings in the Group Policy Editor, such as disabling macro settings, blocking specific file types, or restricting access to certain features.
How to block Office applications from creating executable content using Intune
First, you'll need to make sure Microsoft Defender Antivirus is turned on as the primary antivirus solution, with Real-Time Protection enabled. To verify Defender Antivirus is turned on with real-time protection enabled go to Security recommendations and search for "Turn on real-time protection". From there click "Turn on real-time protection". Finally, click Exposed devices.

Now that we know our devices are ready, let's go ahead and block Office applications from creating executable content using Intune.

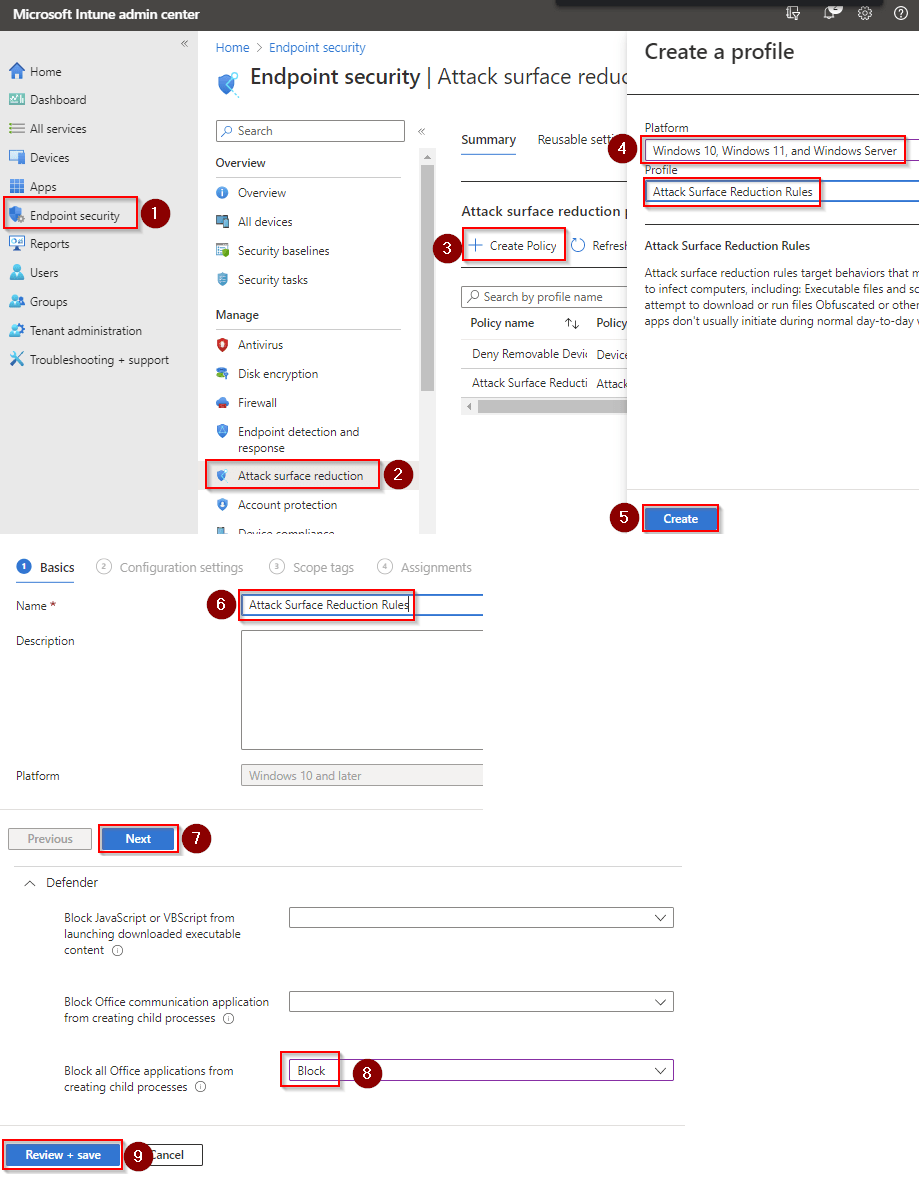
- Go to Microsoft Intune admin center (Microsoft Endpoint Manager) > Endpoint security > Attack surface reduction.
- Click Create Policy.
- Set Platform to Windows 10 Windows 11, and Windows Server.
- Set Profile to Attack Surface Reduction Rules.
- Click Create.
- Name your policy and click Next.
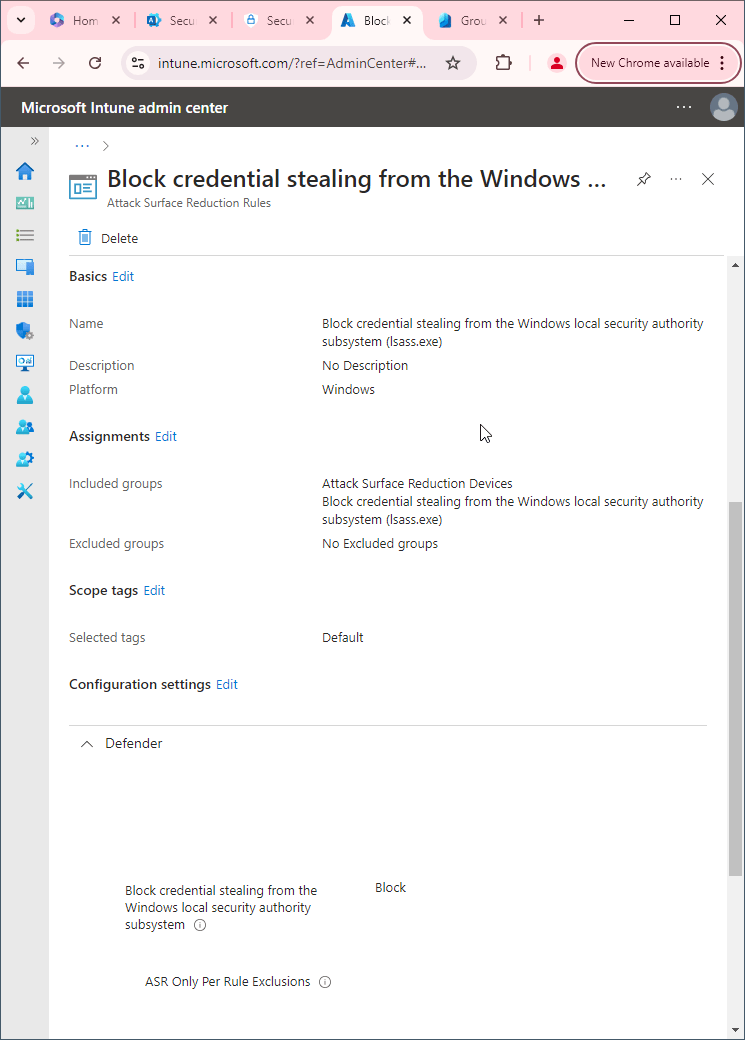
- Set Block Office applications from creating executable content to Block. Click Next.
- Add your inclusions and exclusions. Click Next > Next > Create.