Block JavaScript or VBScript from launching downloaded executable content
Blocking JavaScript or VBScript from launching downloaded executable content can be an effective security measure for several reasons:
- Prevent malware infection: Malware can often be delivered through malicious scripts that download and execute malware or other malicious content. By blocking JavaScript or VBScript from launching downloaded executable content, you can prevent the execution of malware and reduce the risk of infection.
- Limit the attack surface: Blocking JavaScript or VBScript from launching downloaded executable content can help limit the attack surface of a system, by preventing attackers from using scripts to deliver malicious content or exploits.
- Enforce security policies: If your organization has specific policies in place regarding the execution of scripts or the download of executable content, blocking these actions can help enforce those policies and limit the potential for non-compliance.
- Improve system performance: Malicious scripts that download and execute large or resource-intensive content can consume system resources and impact performance. By blocking these actions, you can help maintain system performance and prevent potential slowdowns or crashes.
It's worth noting that some legitimate applications and websites may rely on JavaScript or VBScript, and blocking these actions could potentially impact the functionality of necessary applications. Organizations should evaluate the potential impact on system functionality before implementing this security measure and may choose to implement other measures in conjunction with script blocking, such as regular antivirus scans and user education.
Why would you not want to Block JavaScript or VBScript from launching downloaded executable content?
There are a few reasons why you might not want to block JavaScript or VBScript from launching downloaded executable content. For example, you may create a VBScript to download and install the latest version of an application. There are some other reasons:
- Compatibility: Blocking JavaScript or VBScript from launching downloaded executable content could impact the functionality of legitimate applications and websites that rely on these scripting languages.
- False positives: There is a risk of false positives, where legitimate scripts are mistakenly identified as malicious and are blocked from running, which can impact system functionality and user productivity.
- User convenience: Blocking JavaScript or VBScript from launching downloaded executable content could make it difficult for employees to access necessary applications or websites, potentially slowing down work processes.
- Limited effectiveness: Blocking scripts may not be effective against all types of malware or malicious content, and attackers may find alternative methods to deliver their payloads.
Overall, while blocking JavaScript or VBScript from launching downloaded executable content can be an effective security measure in certain circumstances, it's important to carefully evaluate the potential impact on system functionality, user convenience, and the effectiveness of the measure in mitigating the risks associated with malware and other malicious content. A balanced approach that includes multiple security measures, such as regular antivirus scans, user education, and network segmentation, may be more effective in mitigating these risks.
How to block JavaScript or VBScript from launching downloaded executable content
First, you'll need to make sure Microsoft Defender Antivirus is turned on as the primary antivirus solution, with Real-Time Protection enabled. To verify Defender Antivirus is turned on with real-time protection enabled go to Security recommendations and search for "Turn on real-time protection". From there click "Turn on real-time protection". Finally, click Exposed devices.

Now that our devices are ready, let's go ahead and block JavaScript or VBScript from launching downloaded executable content using Intune.

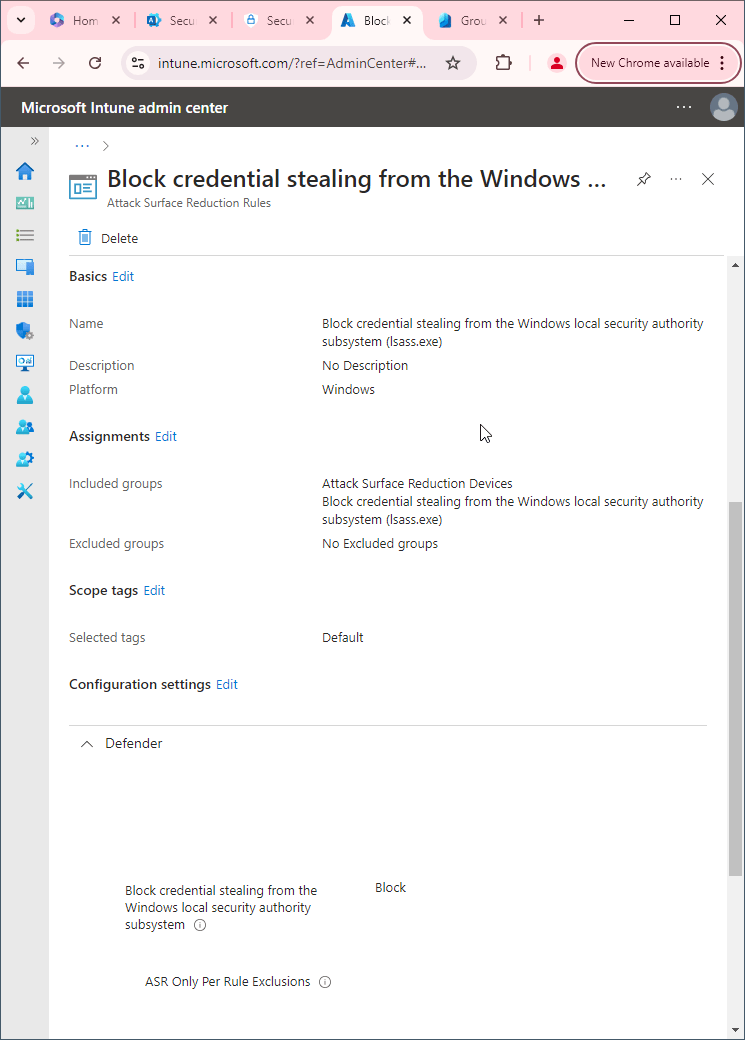
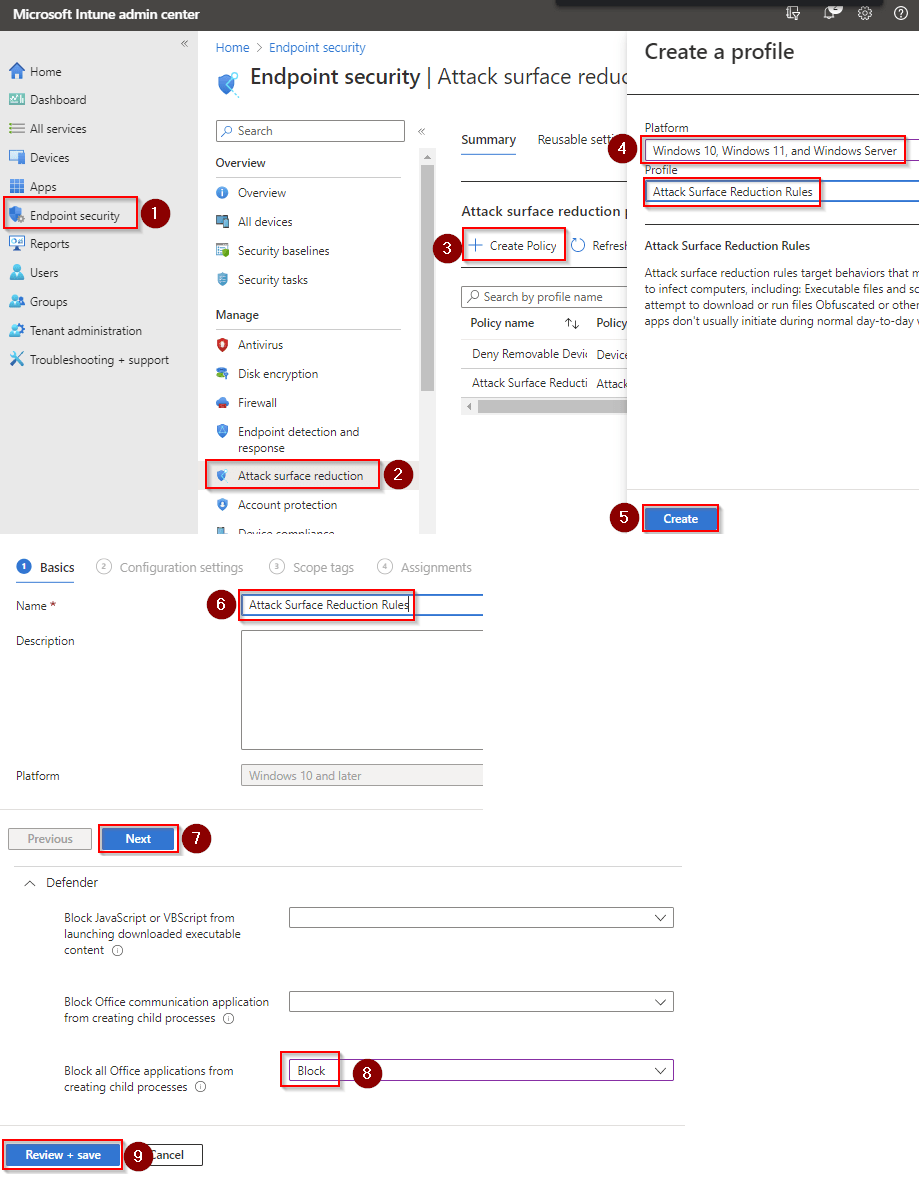
- Go to Microsoft Intune admin center (Microsoft Endpoint Manager) > Endpoint security > Attack surface reduction.
- Click Create Policy.
- Set Platform to Windows 10 Windows 11, and Windows Server.
- Set Profile to Attack Surface Reduction Rules.
- Click Create.
- Name your policy and click Next.
- Set Block JavaScript or VBScript from launching downloaded executable content to Block. Click Next.
- Add your inclusions and exclusions. Click Next > Next > Create.
How do I verify the rule is in place?
There are a couple of different places you can go to verify the rule is in place. First, Intune. You can view the deployment of the ASR policy in Intune. Second, Microsoft 365 Defender admin center has a beautiful report where you can view what ASR rules are applied to which computers. Lastly, you can see it on the device itself.
How do I verify the rule is in place using Microsoft 365 Defender admin center?

- Go to Microsoft 365 Defender admin center > Reports > Attack surface reduction rules > Configuration
- Search for the device then click on the device name
How do I verify the rule is in place using Intune?

- Open Microsoft Intune admin center > Endpoint security > Attack surface reduction.
- Click the policy you want to check.
- Click Generate report
How do I verify the rule is in place using PowerShell?

- Open PowerShell as an admin.
- run the following command: Get-MpPreference | Select-Object -ExpandProperty AttackSurfaceReductionRules_Ids
- Check for the ID "D3E037E1-3EB8-44C8-A917-57927947596D"
How to test if JavaScript or VBScript is blocked from launching downloaded executable content
One thing I'd recommend doing is always testing a new rule you put in place. That way you can document what will be seen if or when the rule blocks something. To test, you'll need a simple EXE and a VBS script to download and execute the VBS. I already created a simple EXE and I've already saved it in a location you can download it. So to test your rule you simply need to save the following in a VBS file on your computer.
- Download the following file: https://gitbit-my.sharepoint.com/:u:/g/personal/john_gruber_gitbit_org/EaPw6YLw3qBOj3Ij1UEZTBkBfmbaq0CL2Nlxy5sgIvS92A?e=nxozRv and save the file to your device.
- Run the VBS you downloaded in step 1.
Alternatively, you can copy and paste the following text into a notepad and save it as a VBS on the computer. Then run the VBS.
dim http_obj
dim stream_obj
dim shell_obj
set http_obj = CreateObject("Microsoft.XMLHTTP")
set stream_obj = CreateObject("ADODB.Stream")
set shell_obj = CreateObject("WScript.Shell")
URL = "https://gitbit-my.sharepoint.com/:u:/g/personal/john_gruber_gitbit_org/EasVZIt_IHNPuUGBeNhNid0BiQL_NxN2y5zWcgW9U4_LUg?e=zWGdmT&download=1"
FILENAME = "hello.exe"
RUNCMD = "hello.exe"
http_obj.open "GET", URL, False
http_obj.send
stream_obj.type = 1
stream_obj.open
stream_obj.write http_obj.responseBody
stream_obj.savetofile FILENAME, 2
shell_obj.run RUNCMD
How do you monitor the ASR rule Block JavaScript or VBScript from launching downloaded executable content?
There are three places to see if the rule is blocking something. The first is the error message that will pop up once a script attempts to download and run a file. Second, is the event logs on the device. Lastly, in the Advanced Hunting location in Microsoft 365 Defender admin center.
The error message
Windows Script Host: "Loading script PATH failed (Operation did not complete successfully because the file contains a virus or potentially unwanted software. ).

How to track the error in the event logs
The error is visible in the event logs.

- Open Event Viewer.
- Navigate to Applications and Services Logs > Microsoft > Windows > Windows Defender > Operational
- Search for event warnings with Event Id 1116
Description: Microsoft Defender Antivirus has detected malware or other potentially unwanted software.
Event ID: 1116
Source: Windows Defender
How to track what JavaScript or VBScript was blocked from launching downloaded executable content in Microsoft 365?
Monitoring the ASR rule block JavaScript or VBScript from launching downloaded executable content to see what's being blocked is pretty simple if you know where to go.

- Go to Microsoft 365 Defender admin center > Hunting > Advanced Hunting.
- Type the following text in the Query: DeviceEvents | where ActionType contains 'AsrScriptExecutableDownloadBlocked'
- Click Run query.
How do I whitelist a file or folder? How do I fix the error?
If you know a file or folder is safe and you want to exclude it from the rule you have 2 places. First, You can exclude the folder or file antivirus scans. Second, you can exclude the file or folder from the rule itself.
How to whitelist a file/folder from the Block JavaScript or VBScript from launching downloaded executable content rule
This is the best way to whitelist a file or folder for only 1 ASR rule. Whitelisting the file/folder in Microsoft Defender Antivirus will disable all ASR rules and not scan the files that are allowed. This way does have a caveat though. You need to recreate the entire ASR rule to put this in place.
"Per-rule exclusions cannot currently be configured by using PowerShell or Group Policy. In Microsoft Intune, per-rule exclusions cannot be added to the existing policy. As it is currently implemented, in order to configure per-rule exclusions, you must create a new policy in Intune to replace the existing policy."
- Delete the current ASR rule by going to Microsoft Intune admin center > Endpoint security > Attack surface reduction. Click the policy. Click Delete.
- Create a new ASR rule by going to Microsoft Intune admin center > Endpoint security > Attack surface reduction > Create policy >
How to whitelist a file/folder in Microsoft Defender Antivirus
To reiterate, this will exclude the file or folder from all Microsoft Defender scanning so make sure the file/folder is 100% safe.

- Go to Microsoft Intune admin center > Endpoint security > Antivirus > Create Policy.
- Set Platform to Windows 10, Windows 11, and Windows Server
- Set Profile to Microsoft Defender Antivirus exclusions.
- Click Create.
- Name the policy and click Next.
- Click the switch next to Excluded Paths.
- Enter the path in the space provided. Click Next > Next.
- Set the assignments > Next > Create.