Block execution of potentially obfuscated scripts
Obfuscated scripts are code written in a way that is intentionally difficult to understand or analyze. The purpose of obfuscation is to hide the true purpose and functionality of the code from automated security tools and analysts, making it more difficult to detect and analyze any malicious activity.
Obfuscation techniques can include things like:
- Renaming variables and functions to obscure their true purpose and function
- Inserting meaningless statements or comments into the code
- Encoding the code using techniques such as base64 or hexadecimal encoding
- Breaking the code into small fragments that are combined at runtime
- Using encryption to hide the true purpose of the code
Obfuscation can be used by attackers to bypass security controls and deliver malware to a system. It can also be used by legitimate software developers to protect intellectual property or prevent reverse engineering.
However, because obfuscated code can be difficult to analyze and understand, it can be challenging for security teams to identify and respond to any malicious activity associated with that code. As a result, some security measures may include blocking the execution of potentially obfuscated scripts as a way to limit the potential for security incidents.
Why would you not want to block the execution of potentially obfuscated scripts?
There are a few reasons why you might not want to block the execution of potentially obfuscated scripts:
- Application functionality: Some legitimate applications may use obfuscation techniques to protect intellectual property or prevent reverse engineering. Blocking the execution of potentially obfuscated scripts could prevent these applications from functioning properly.
- False positives: Obfuscation can be used for legitimate purposes, and blocking the execution of all potentially obfuscated scripts could result in false positives, where legitimate scripts are blocked, and legitimate applications are prevented from functioning.
- Limited effectiveness: Blocking the execution of potentially obfuscated scripts may not be the most effective security measure, as attackers can often use other techniques to evade detection and deliver malware. Instead, organizations may choose to focus on implementing a range of other security measures, such as email filtering, web content filtering, and regular patching and updates, to mitigate the risk of malicious activity.
- System compatibility: Blocking the execution of potentially obfuscated scripts could cause compatibility issues with other applications or processes on the system that rely on those scripts to function properly.
Overall, the decision to block the execution of potentially obfuscated scripts will depend on the specific security risks and threats facing a system and the potential impact on system functionality. Organizations should carefully evaluate the effectiveness of this security measure and consider alternative measures before implementing it.
How to block execution of potentially obfuscated scripts
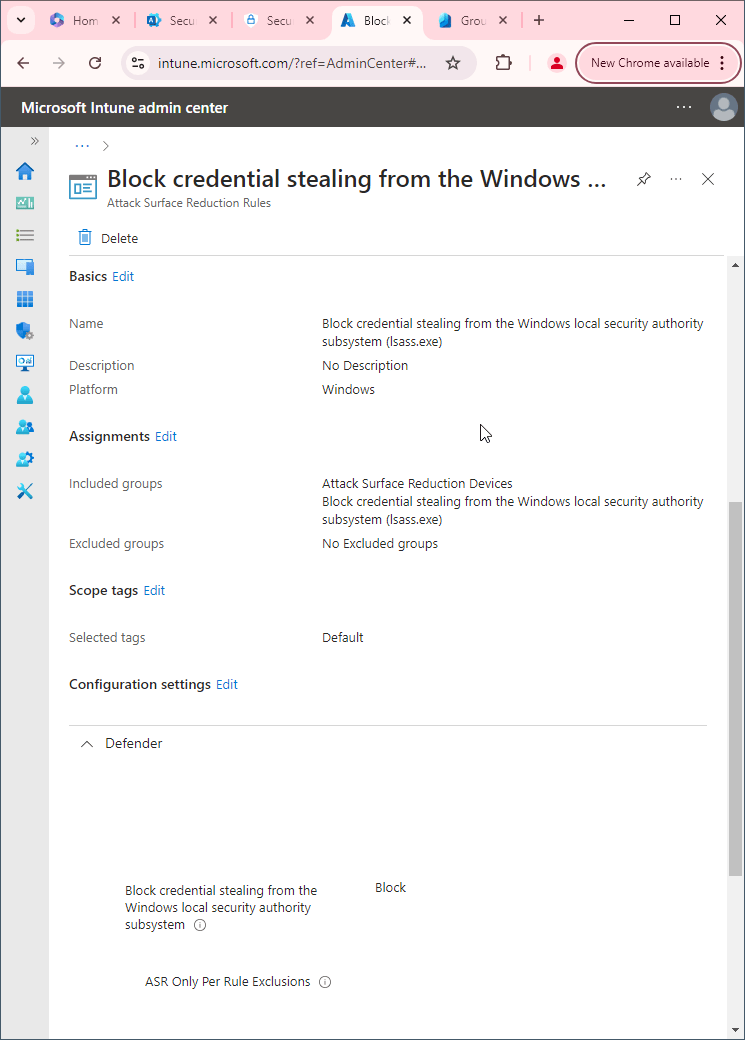
First, you'll need to make sure Microsoft Defender Antivirus is turned on as the primary antivirus solution, with Real-Time Protection enabled. To verify Defender Antivirus is turned on with real-time protection enabled go to Security recommendations and search for "Turn on real-time protection". From there click "Turn on real-time protection". Finally, click Exposed devices.

Now that our devices are ready, let's go ahead and block the execution of potentially obfuscated scripts using Intune.

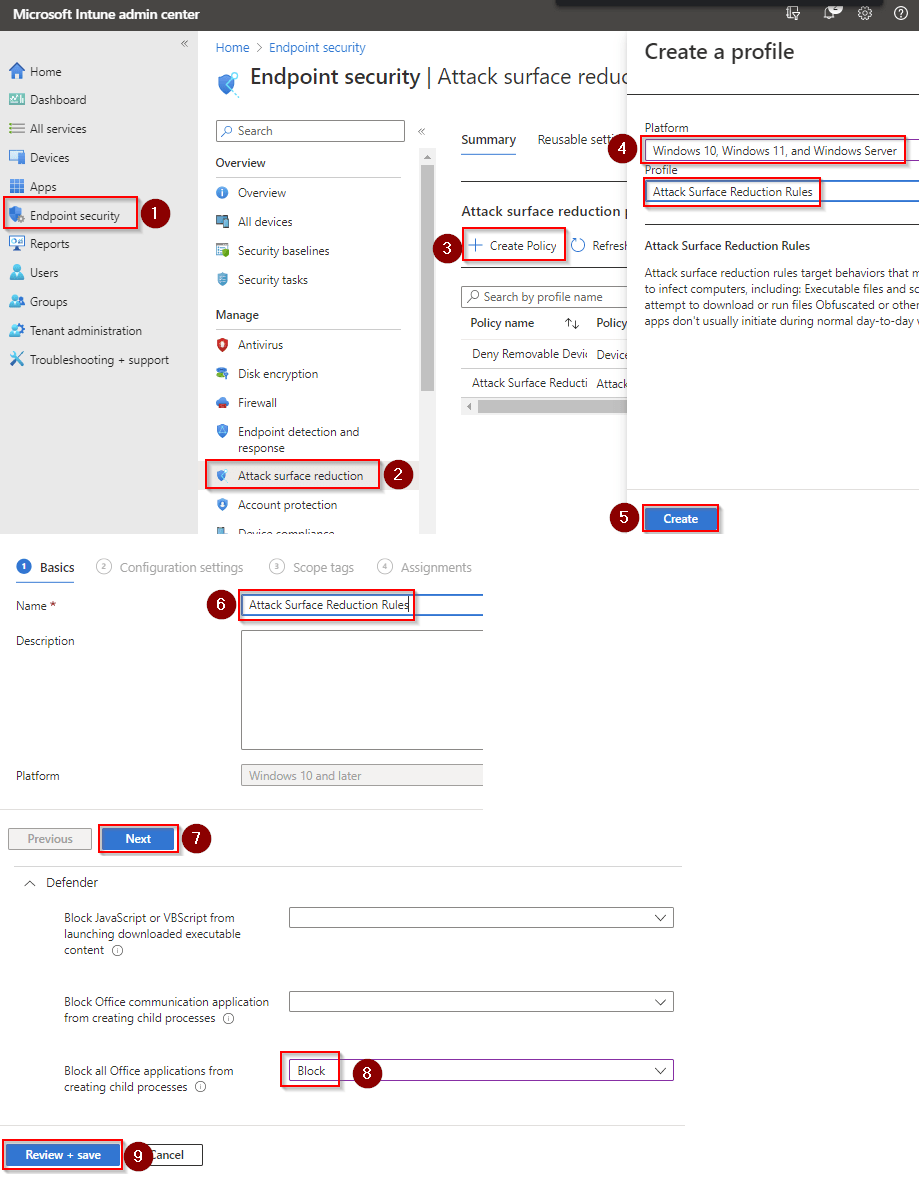
- Go to Microsoft Intune admin center (Microsoft Endpoint Manager) > Endpoint security > Attack surface reduction.
- Click Create Policy.
- Set Platform to Windows 10 Windows 11, and Windows Server.
- Set Profile to Attack Surface Reduction Rules.
- Click Create.
- Name your policy and click Next.
- Set Block execution of potentially obfuscated scripts to Block. Click Next.
- Add your inclusions and exclusions. Click Next > Next > Create.