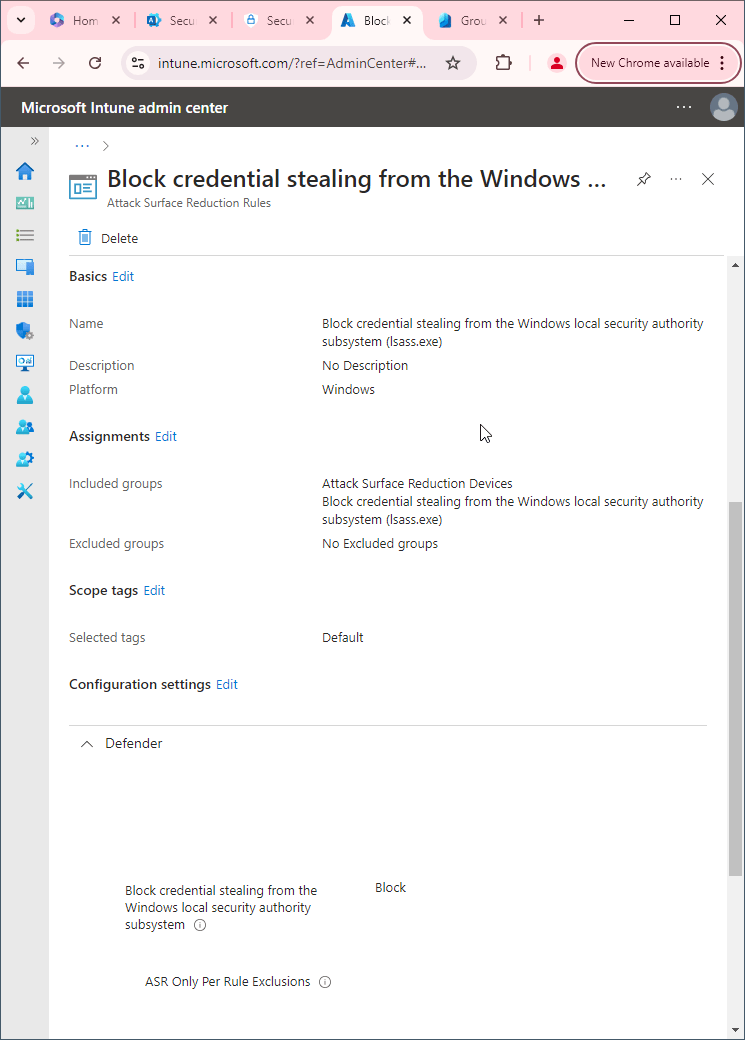
Block executable files from running unless they meet a prevalence, age, or trusted list criterion
Blocking executable files from running unless they meet certain criteria, such as prevalence, age, or a trusted list, can help improve the security of a system by preventing the execution of potentially malicious software. Here are some reasons why this might be done:
Malware prevention: By blocking executables that do not meet certain criteria, organizations can reduce the risk of malware infection on their systems. For example, they may block the execution of files that are not commonly used or that are older than a certain age, as these are more likely to be malicious.
Compliance: Certain regulatory frameworks, such as the Payment Card Industry Data Security Standard (PCI DSS), require organizations to implement controls to prevent the execution of unauthorized software.
Endpoint protection: Endpoint protection solutions may use prevalence, age, or trusted list criteria to determine whether to allow or block the execution of an executable file, in order to prevent attacks on endpoints such as laptops, desktops, and mobile devices.
Insider threat prevention: Blocking the execution of unauthorized software can help prevent insider threats, where an employee intentionally or unintentionally introduces malware onto the system.
In general, blocking executable files from running unless they meet certain criteria can help improve the overall security posture of an organization, but it is important to ensure that these controls do not adversely impact legitimate business operations. Therefore, it is important to carefully consider the criteria used to block executables and to monitor and adjust these controls as necessary.
Why would you not block executable files from running unless they meet a prevalence, age, or trusted list criterion?
Depending on the environment I don't always recommend enabling this feature. When users typically install software on their own computers this ASR rule will simply get in the way. Here are some other reasons why this might be the case:
- Legitimate software: Blocking executables based solely on criteria like prevalence or age could inadvertently prevent legitimate software from running on the system. For example, some older software may still be critical to business operations but would be blocked if the age criterion is set too low.
- False positives: Blocking executables based on criteria like prevalence or age can also result in false positives, where a legitimate executable is incorrectly identified as being malicious or unauthorized.
- User productivity: Blocking executables could hinder user productivity by preventing them from using software that they need to perform their work. This can lead to frustration and decreased efficiency.
- Compatibility: Some software may require certain executables to run in order to function properly, and blocking those executables could cause compatibility issues.
In general, it is important to carefully consider the potential impacts of blocking executable files from running based on certain criteria. Organizations should implement appropriate security controls to prevent the execution of malicious or unauthorized software while also ensuring that legitimate software can still run without hindrance. This may involve using other security controls, such as endpoint protection solutions or security awareness training for users.
How to block executable files from running unless they meet a prevalence, age, or trusted list criterion
First, you'll need to make sure Microsoft Defender Antivirus is turned on as the primary antivirus solution, with Real-Time Protection enabled. To verify Defender Antivirus is turned on with real-time protection enabled go to Security recommendations and search for "Turn on real-time protection". From there click "Turn on real-time protection". Finally, click Exposed devices.

Next, you need to verify that cloud-delivered protection is enabled in your organization. To verify that cloud-delivered protection is enabled go to Security recommendations and search for "cloud-delivered protection". From there click on "Enable cloud-delivered protection" and check for exposed devices.

Now that our devices are ready, let's go ahead and block executable files from running unless they meet a prevalence, age, or trusted list criterion using Intune.

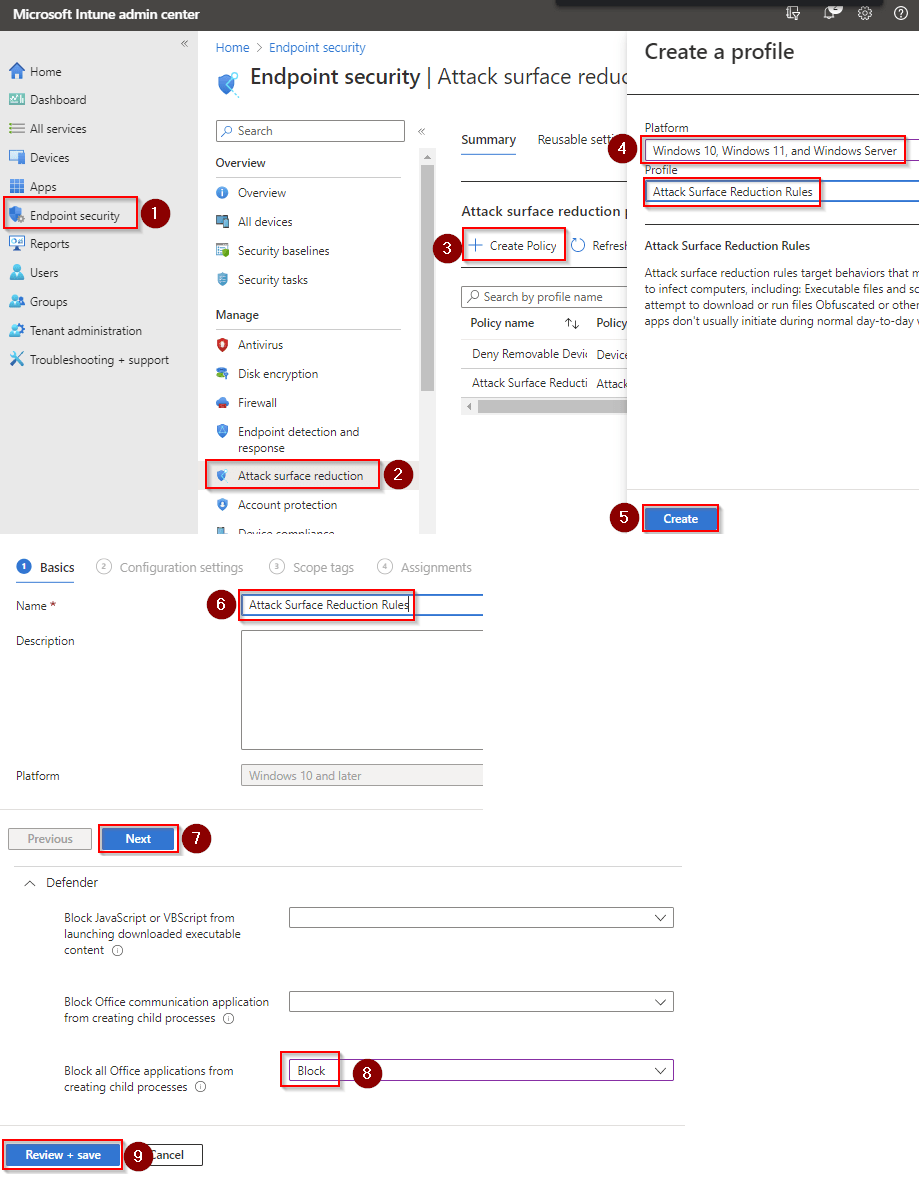
- Go to Microsoft Intune admin center (Microsoft Endpoint Manager) > Endpoint security > Attack surface reduction.
- Click Create Policy.
- Set Platform to Windows 10 Windows 11, and Windows Server.
- Set Profile to Attack Surface Reduction Rules.
- Click Create.
- Name your policy and click Next.
- Set Block executable files from running unless they meet a prevalence, age, or trusted list criterion to Block. Click Next.
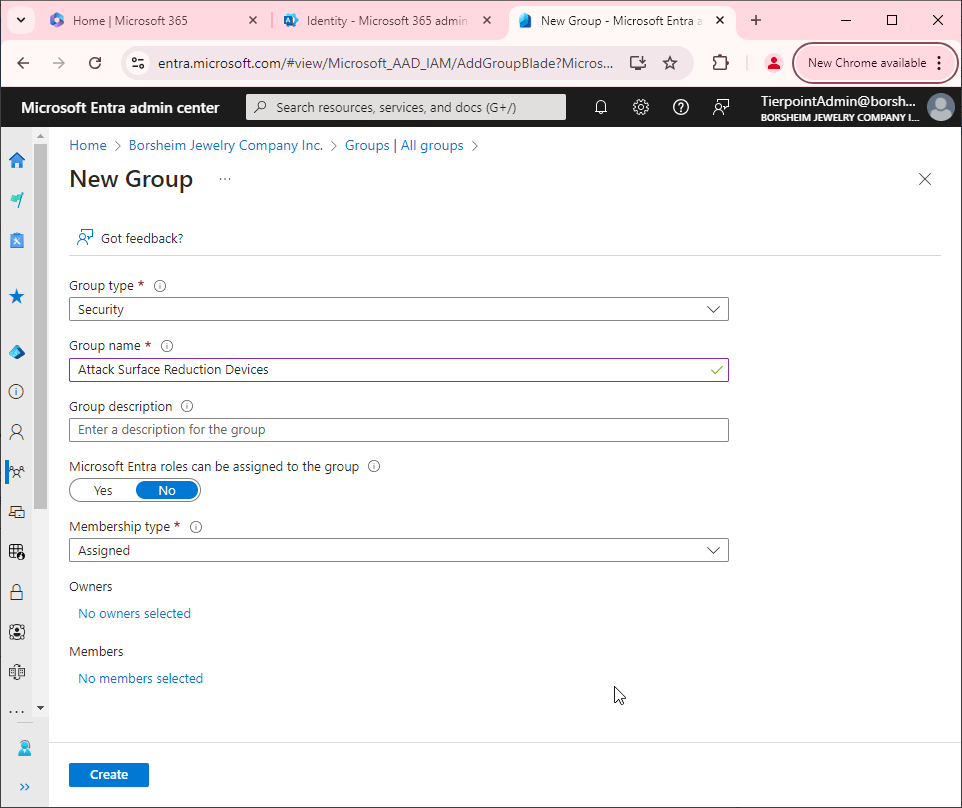
- Add your inclusions and exclusions. Click Next > Next > Create.